AWS Internet Gateway vs NAT Gateway

by Valts Ausmanis · September 26, 2024
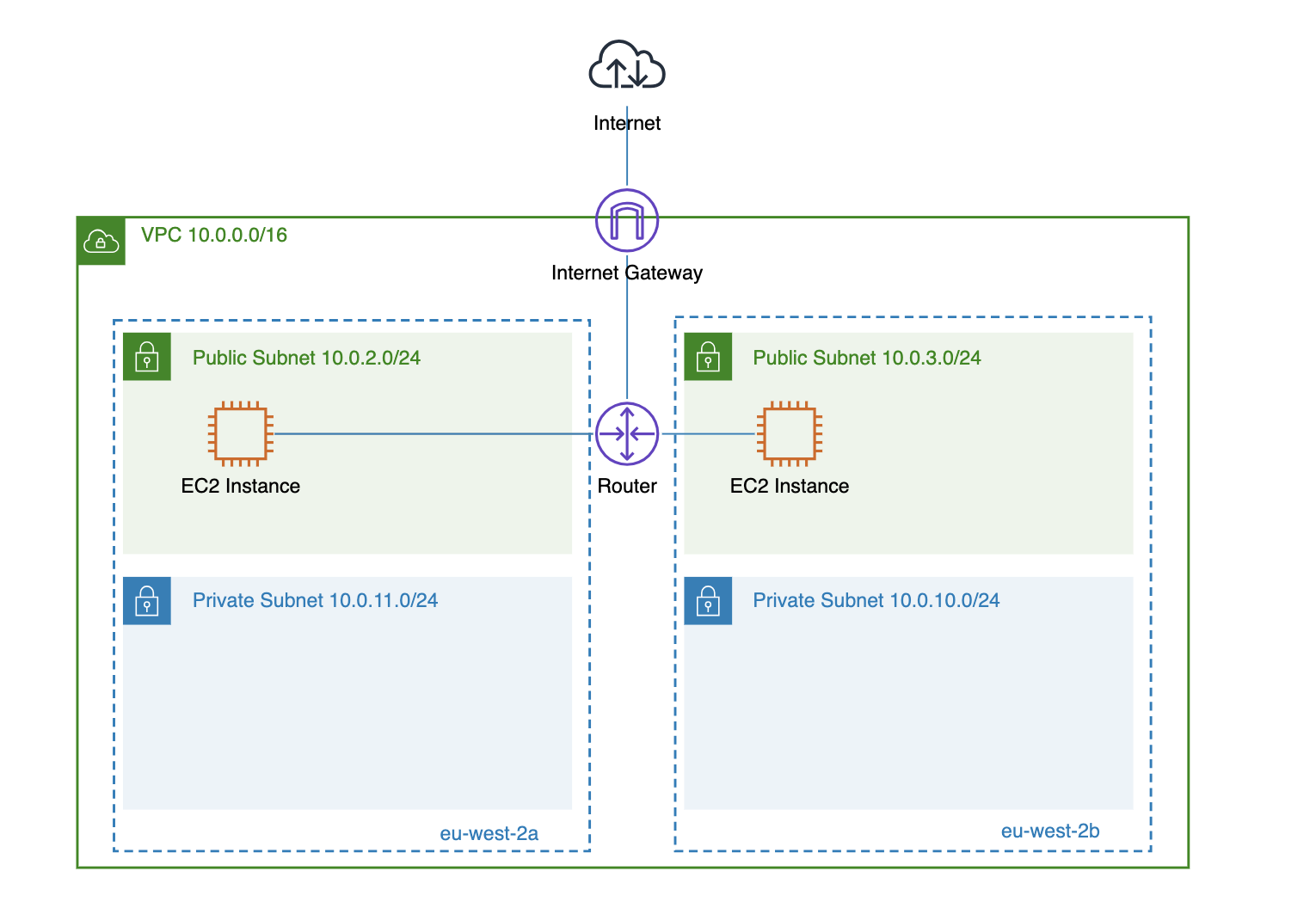
Both the AWS Internet Gateway and NAT Gateway are essential networking resources that ensure your VPC resources, like EC2 instances, can communicate with the public internet. The main difference between the two is that the Internet Gateway enables both inbound and outbound communication with the internet, whereas the NAT Gateway only plays a role in outbound communication. Let’s now take a closer look at the differences between these two and when to use each of these resources.
In This Article
- What is AWS Internet Gateway?
- What is AWS NAT Gateway?
- What are the Differences Between Internet Gateway and NAT Gateway?
- When to Use Each?
What is AWS Internet Gateway?
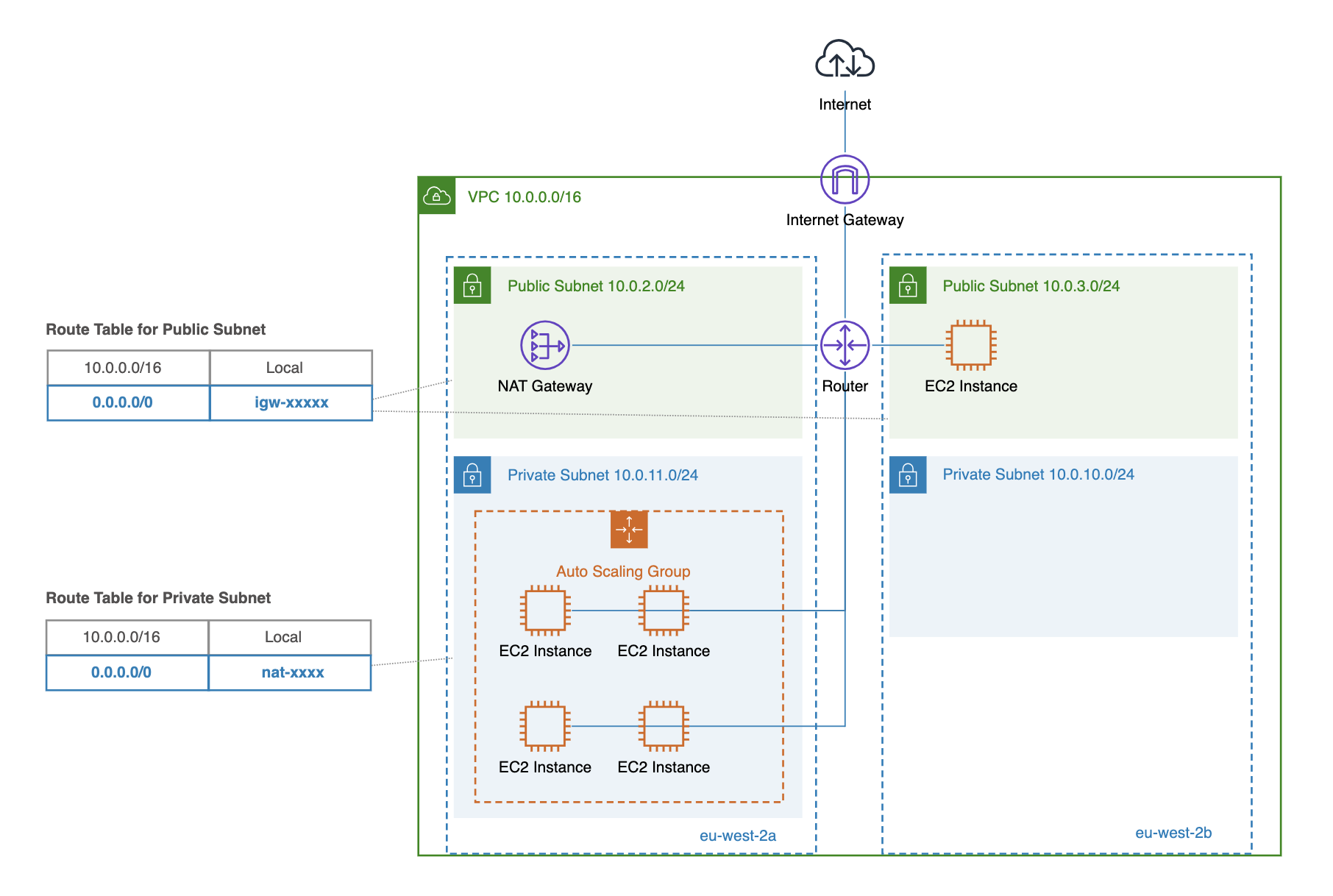
AWS internet gateway is a highly available VPC component that provides internet access to your VPC resources (e.g., EC2 instances, Load Balancers, NAT gateways), supporting both inbound and outbound traffic for instances with public IP addresses.
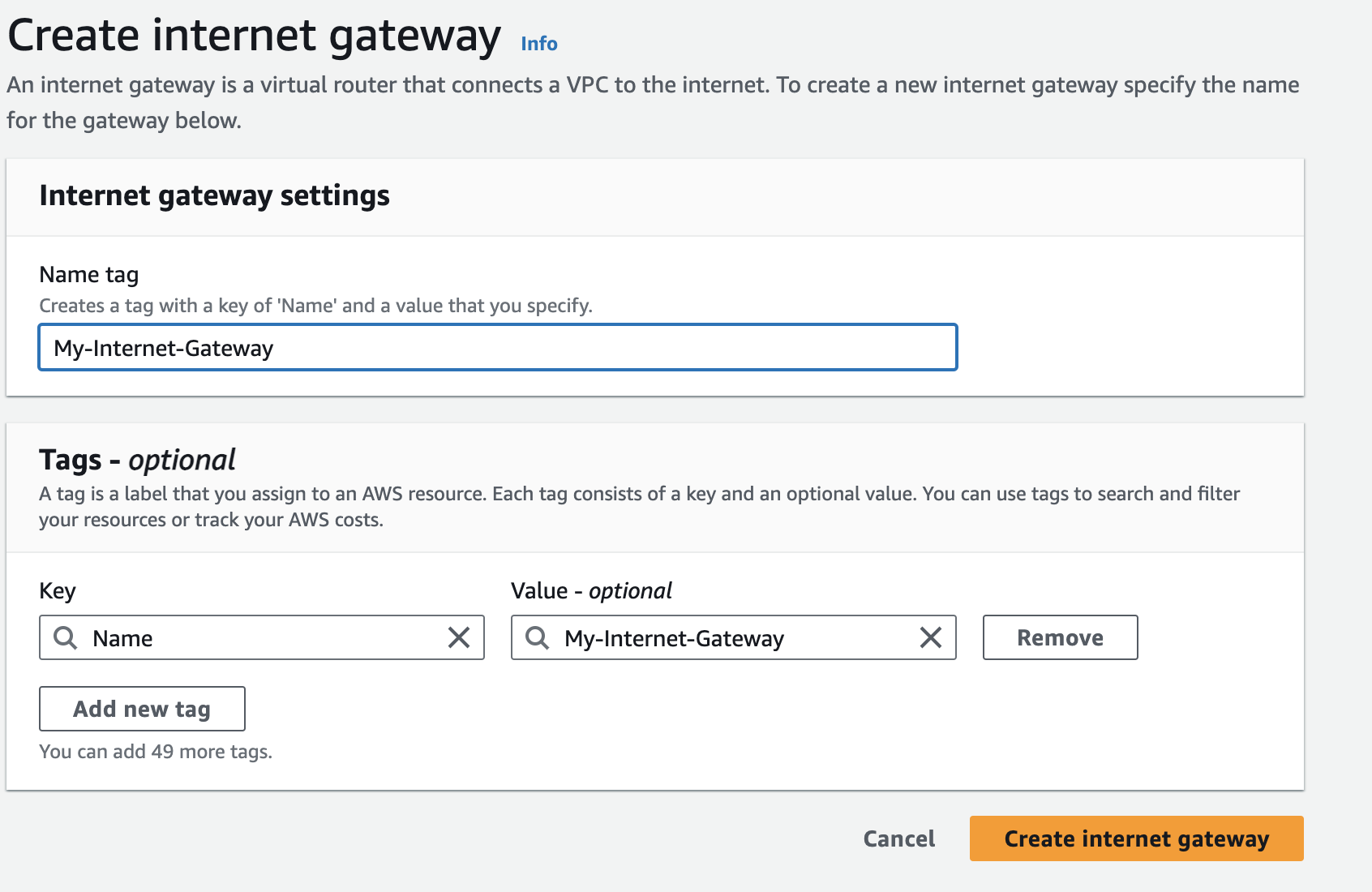
As the internet gateway is fully managed by AWS, the only optional configuration during creation is the name tag:
In order to start to use internet gateway you have to do the following:
- Attach internet gateway to VPC
- Add route
0.0.0.0/0 - igw-xxxxxto your route table for public subnets to route outbound traffic to internet gateway. Keep in mind that only instances that have public IPv4 or IPv6 address can send outbound traffic to internet gateway. - In order to control inbound or outbound traffic to your instances specific security group rules and network access control lists should be used.
What is AWS NAT Gateway?
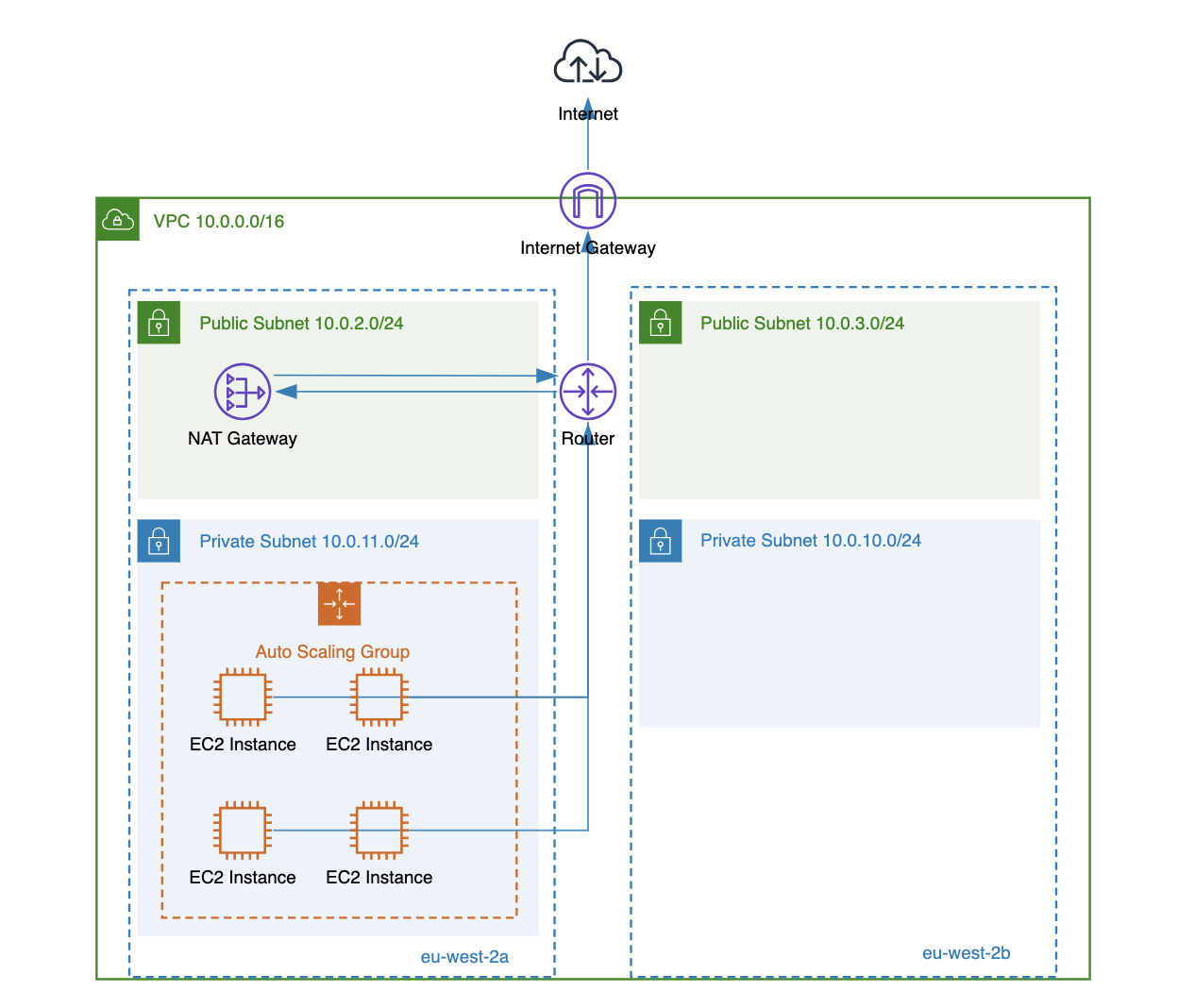
AWS NAT gateway is an AWS managed network address translation (NAT) service mainly used to allow instances in private subnets to connect to the public internet while preventing unsolicited inbound connections from the internet. You can still use public AWS load balancers which can route traffic from the internet to private instances, but this, of course, would be your controlled inbound traffic.
There are two types of NAT gateways:
- Public NAT Gateway: This is used for instances in private subnets to connect to the internet. When creating this type of gateway, an Elastic IP address (public IP) must be assigned, and the NAT gateway must be provisioned in a public subnet (which has a route to an internet gateway). If a public NAT gateway is deployed in a private subnet (yes, the AWS console allows this), the NAT gateway will not be able to route traffic to the internet gateway.
- Private NAT Gateway: This can be used for private instances to connect to other VPCs or an on-premises network. Always double-check your AWS network architecture before using private NAT gateways, as they add extra cost and latency due to the additional hop, compared to routing traffic directly from your EC2 instance to a VPC peering connection or VPN gateway. You should only use a private NAT gateway if the destination (e.g., on-premises networks) only allows connections from a specific or limited IP address range (allow-listed IP addresses). In this case, traffic routed through the private NAT gateway would originate from the gateway's private IP address.
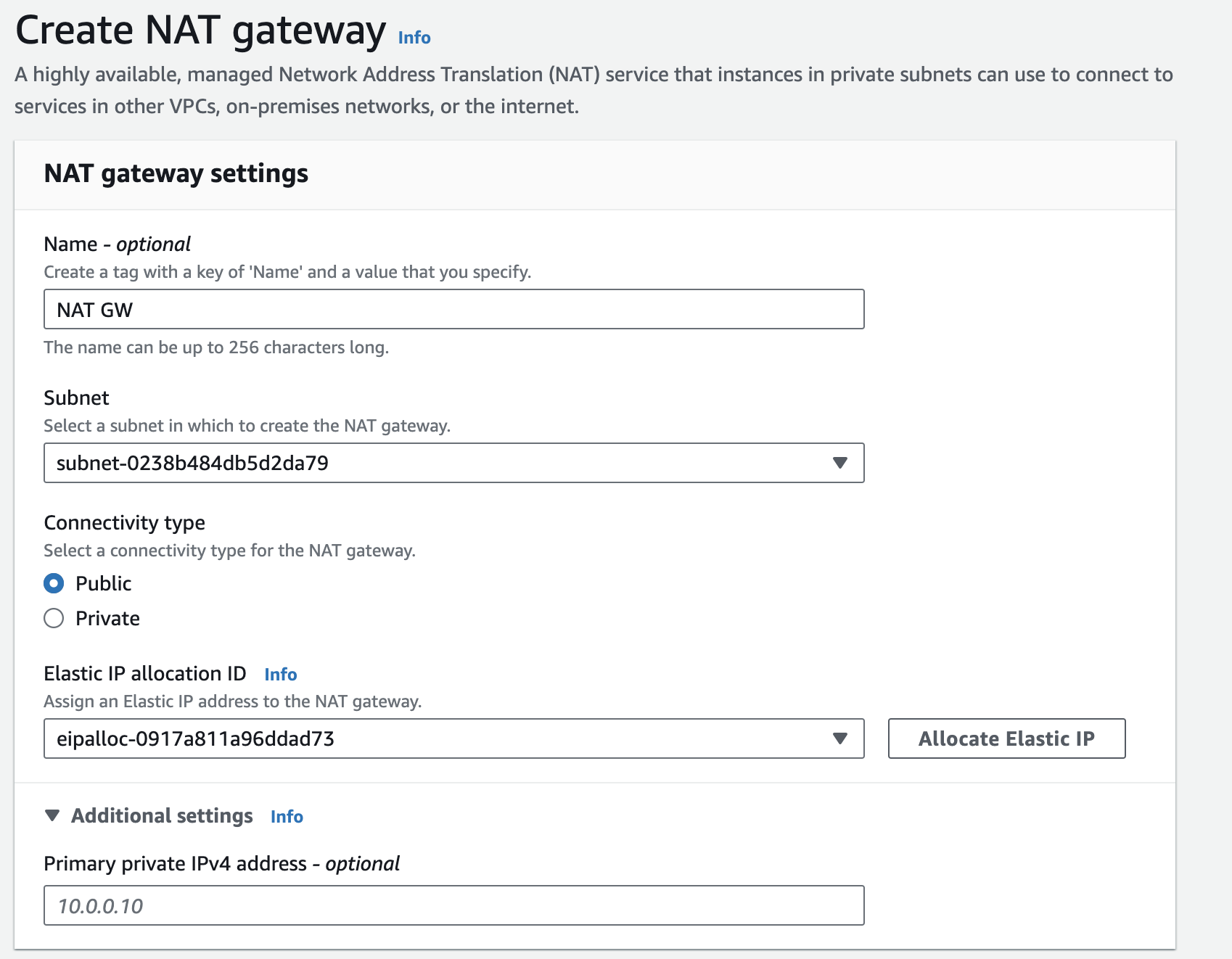
To start using a public NAT gateway after creating it:
- Add the route
0.0.0.0/0 - nat-xxxxxto your route table for private subnets to allow instances to route traffic through the NAT gateway. - To control outbound traffic from your instances, specific security group rules and network access control lists (NACLs) should be applied.
What are the Differences Between Internet Gateway and NAT Gateway?
There are differences between the internet gateway and NAT gateway, which we will now describe in more detail. This will help us better understand when to use each of these AWS networking resources.
Purpose
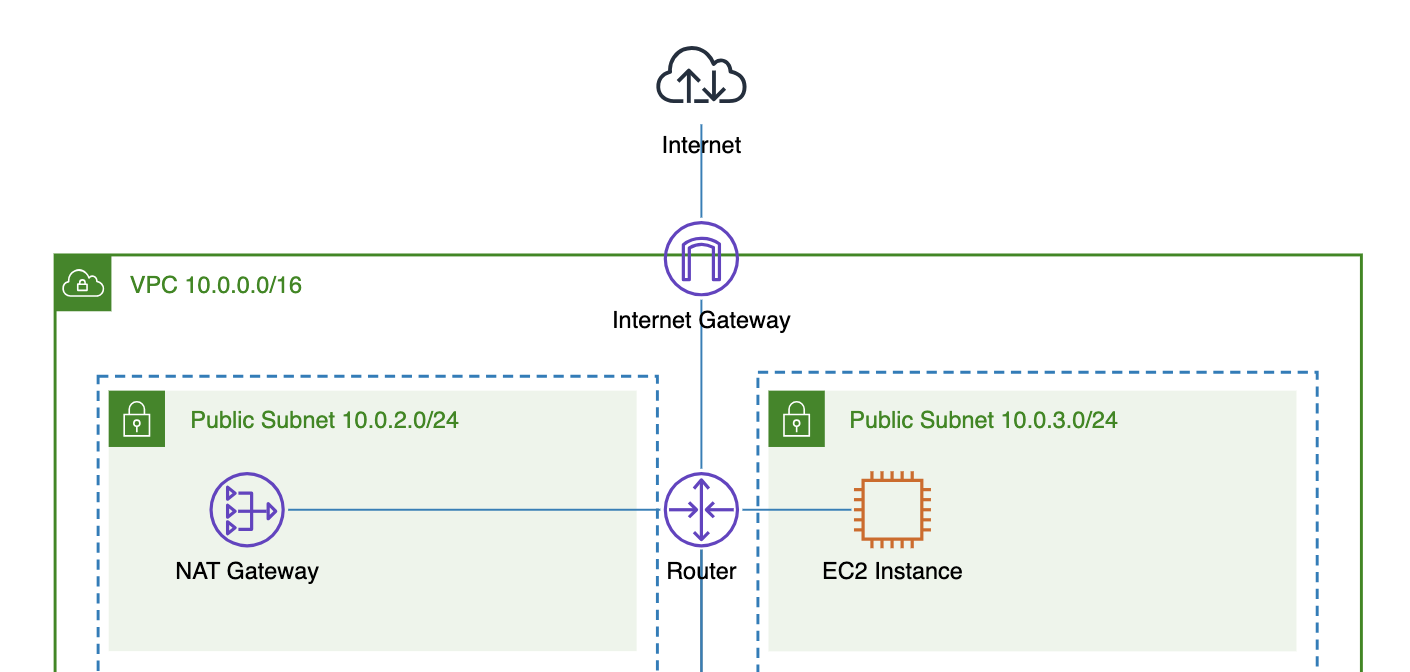
The AWS internet gateway is the main bridge between your VPC and the internet. If an internet gateway is not attached to the VPC, all deployed resources (e.g., EC2 instances, load balancers, Lambda functions, etc.) will not be accessible from the public internet, and vice versa—they will not be able to access any public internet resources either.
However, the NAT gateway acts only as an intermediary for outbound traffic from your private instances, translating private IP addresses to a common public IP address (or a private IP address in the case of a private NAT gateway) and blocking any unsolicited inbound traffic.
Dependency
I have often heard and seen the misleading assumption that the NAT gateway communicates directly with the public internet, but that’s not true. When the NAT gateway receives traffic from your private instances (e.g., EC2 instances), this traffic must be routed to an internet gateway in order to reach the public internet.
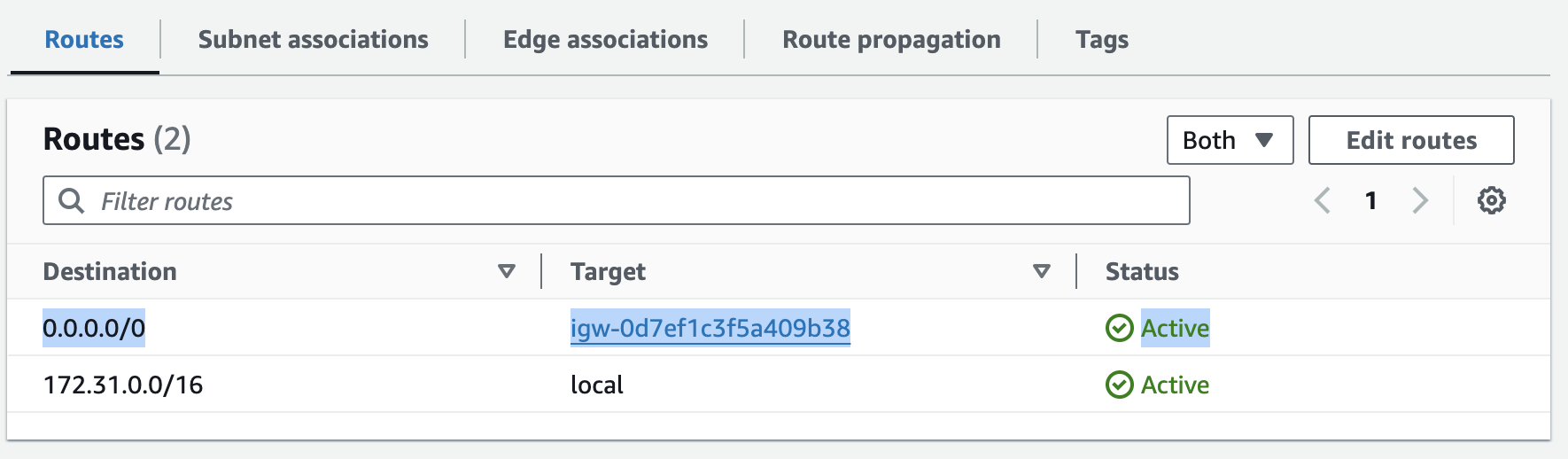
Without this route to the internet gateway, the traffic will be stuck inside the VPC. The public NAT gateway will use its Elastic IP (public IP address) as the source IP address only when it's connected to an internet gateway in the same VPC.
You can, of course, route traffic from the NAT gateway to a VPN gateway (e.g., to an on-premises network) or a transit gateway (e.g., to other VPCs), but this traffic still won't directly reach the public internet, as it will originate from the private IP address of the NAT gateway.
However, an internet gateway works independently without the need for a NAT gateway to be provisioned.
Traffic Direction
The AWS internet gateway supports both inbound and outbound traffic between VPC resources with public IP addresses (e.g., EC2 instances, load balancers) and the public internet. This means that if an EC2 instance has a public IP address, the subnet has a route to the internet gateway (e.g., 0.0.0.0/0 - igw-xxxxx), and the internet gateway is attached to the VPC, then the instance can be accessible (based on the defined security group rules) for inbound traffic (initiated from the public internet) and can also initiate outbound requests to the public internet.
However, the NAT gateway only supports outbound traffic initiated from your VPC resources (e.g., EC2 instances, Lambda functions). This means that requests initiated from the public internet will never reach private VPC resources (with only private IP addresses) that use the NAT gateway to communicate with the public internet.
Availability
The AWS internet gateway provides high availability by default. This means that if one availability zone goes down, it will still be able to route traffic to other available and active availability zones in your VPC.
However, when using a NAT gateway and deploying resources across multiple availability zones (e.g., EC2 instances in different AZs), you need to create a NAT gateway in each availability zone to achieve high availability. This ensures that your private resources won’t lose internet access if one of the availability zones becomes unavailable.

IPv4/IPv6 vs IPv4 only
Internet gateway supports both IPv4 and IPv6 traffic.
NAT gateway only supports IPv4.
To allow outbound-only IPv6 traffic from instances to communicate with the public internet, you can use an egress-only internet gateway. The egress-only gateway is a highly available VPC component designed specifically for IPv6 traffic.
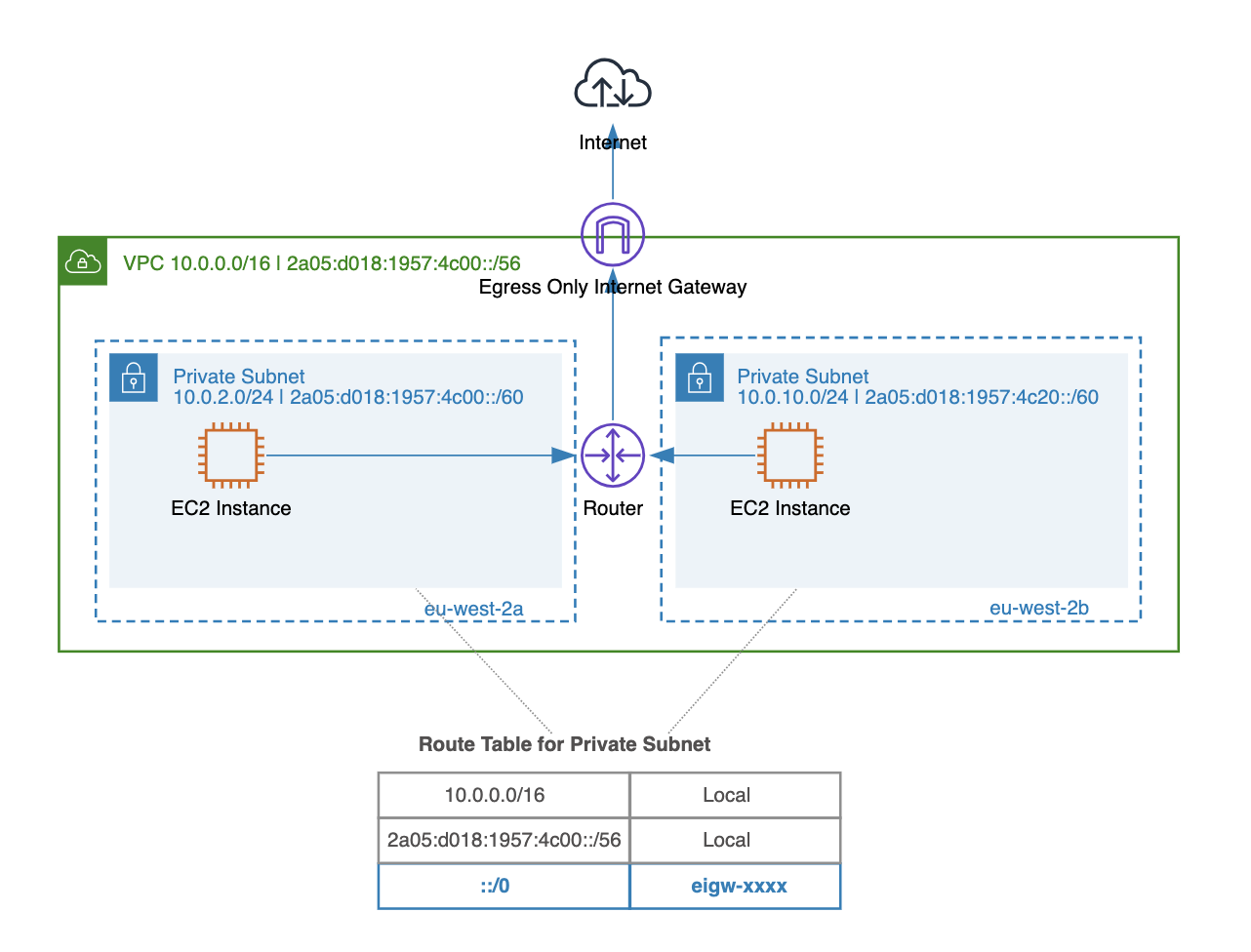
Sharing Across VPCs
One internet gateway cannot be shared across multiple VPCs.
However, a NAT gateway can be indirectly shared across VPCs using transit gateway attachments or VPC peering connections. One use case for this AWS network architecture is to have a central egress VPC with NAT gateways that are shared among multiple spoke VPCs. This means all outbound traffic from these spoke VPCs will be routed through the central egress VPC.
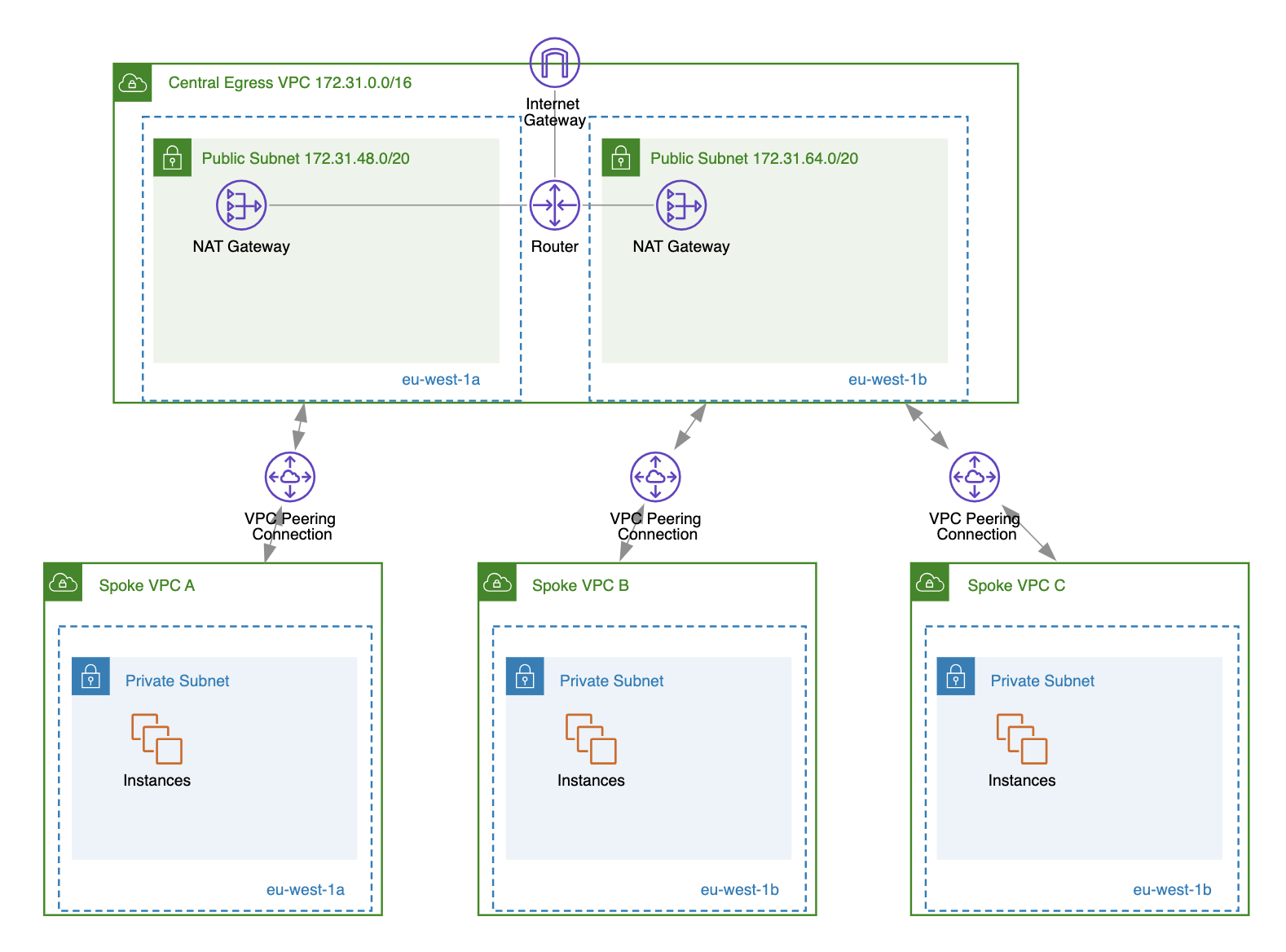
This can provide several benefits, such as:
- Reduced NAT gateway costs: We don’t have to provision NAT gateways in every spoke VPC.
- Simplified management: All outbound internet access goes through one specific VPC, allowing us to implement security policies, logging, and monitoring in one place.
However, before using this AWS network architecture, please consider all the additional costs associated with VPC peering or transit gateway attachment usage.
Cost
For the AWS internet gateway, there are no additional costs associated with its use; only standard data transfer costs apply.
For the NAT Gateway , in addition to standard data transfer costs:
- Price per NAT gateway: $0.045 per hour.
- Data processing charge: $0.045 per GB.
Here you can clearly see that using one NAT Gateway for a whole month (30 days) and processing 100 GB of data would cost around $36.90 ($32.40 for hourly usage + $4.50 for data processing).
When to Use Each?
AWS Internet Gateway should be used whenever your application needs to provide public inbound and outbound traffic, meaning that your application is publicly accessible from the internet (e.g., a web server, API endpoint, or any public-facing service).
The NAT gateway should be used in combination with the internet gateway to provide your private VPC instances (e.g., EC2 instances, Lambda functions) with the ability to connect to public internet resources while preventing unsolicited inbound connections from the internet.
Looking for a tool to automatically visualize your Internet Gateways and NAT Gateways?
Try out Cloudviz.io and visualize your AWS cloud environment in seconds

As experienced AWS architects and developers, our mission is to provide users an easy way to generate stunning AWS architecture diagrams and detailed technical documentation. Join us to simplify your diagramming process and unleash the beauty of your cloud infrastructure
Support
Contact
Copyright © 2019 - 2025 Cloudviz Solutions SIA