12 Best Practices for Using AWS CloudTrail

by Valts Ausmanis · July 12, 2024
Logging user activity and API usage on AWS is a must for any organization. This practice helps meet compliance standards, respond quickly to issues, and keep your AWS accounts secure. Every AWS account has CloudTrail enabled by default, providing management event history for the past 90 days. To maximize the benefits of CloudTrail and enhance your security, it's important to follow some best practices, which we will describe in this article.
In This Article
- What is AWS CloudTrail?
- 12 AWS CloudTrail Best Practices
- Create a Trail in All AWS Accounts and Regions
- Set up Separate Trails for Different Use Cases
- Turn on Data Events for Trails
- Store CloudTrail Events in a Dedicated and Centralized S3 Bucket
- Use CloudTrail Log File Integrity Validation
- Send CloudTrail Events to CloudWatch Logs
- Configure Least Privilege Access to the CloudTrail Logs S3 Bucket
- Enable MFA delete on the CloudTrail Logs S3 Bucket
- Define a Retention Policy for Logs Stored in S3
- Encrypt CloudTrail Log Files at Rest
- Enable Logging on the CloudTrail S3 Bucket
- Limit Usage of the AWSCloudTrail_FullAccess policy
- AWS CloudTrail Costs
- Summary
What is AWS CloudTrail?
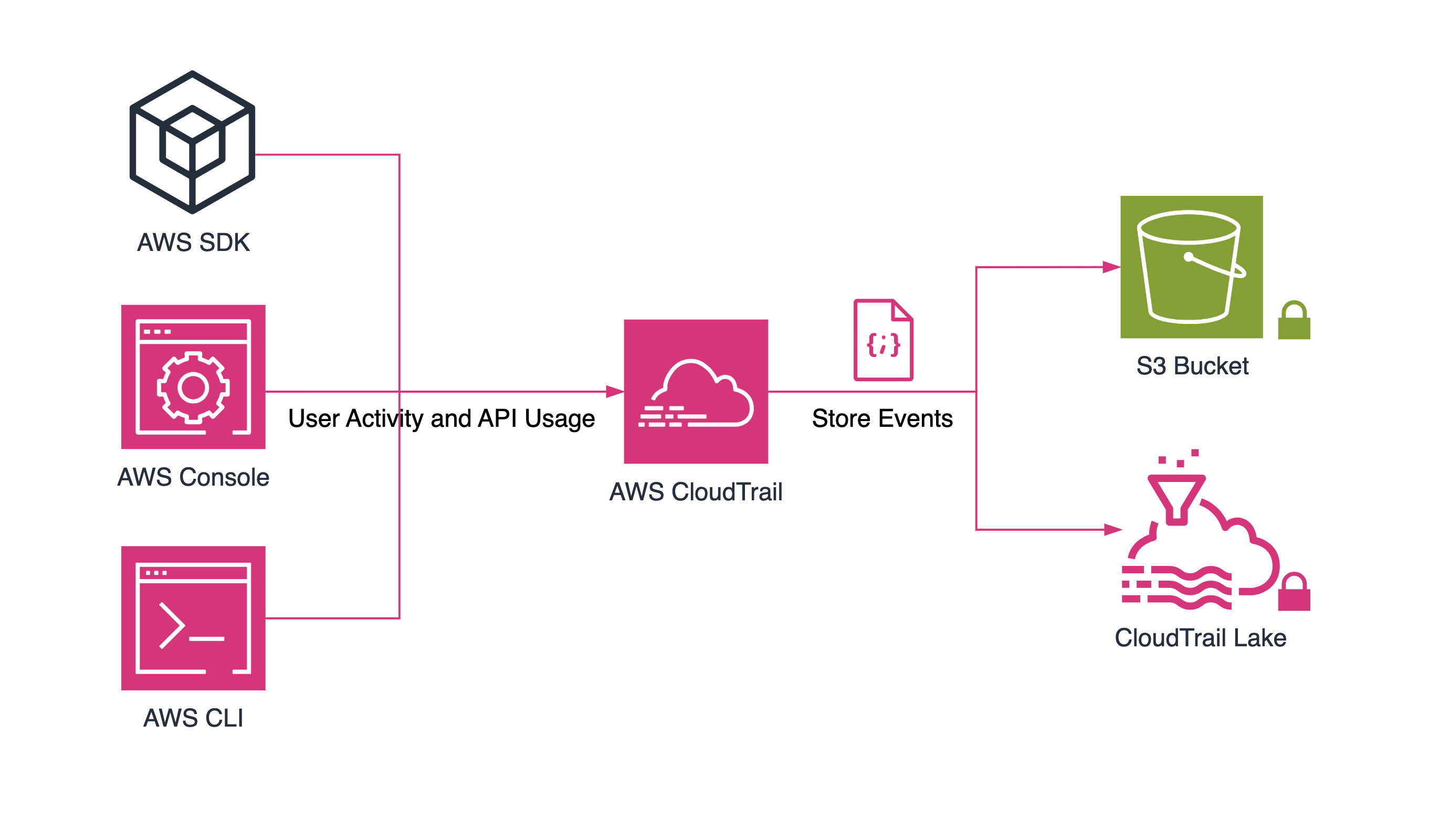
AWS CloudTrail is a service that tracks user activity and API usage on AWS. This activity or usage is stored as an event. Usually, events are created when:
- A user browses the AWS console
- The AWS SDK is used to make calls to other AWS services
- The AWS CLI is used
There are three ways to record events in AWS CloudTrail:
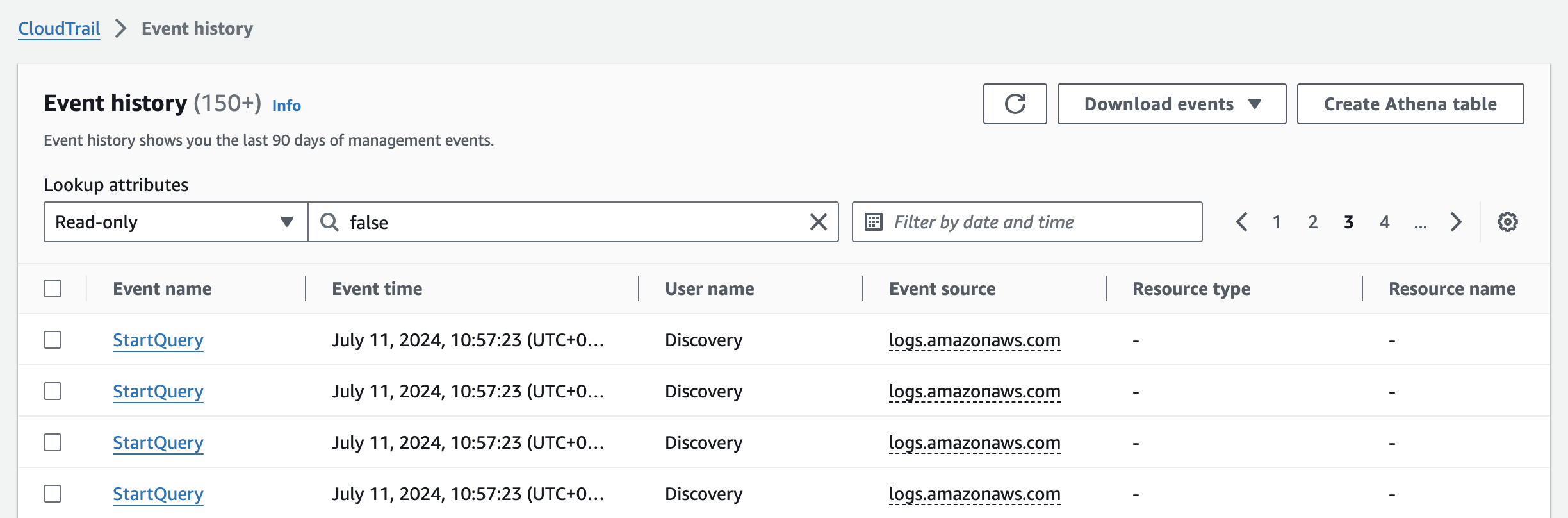
- Event history, which is enabled by default for every AWS account and provides 90 days of management event history.
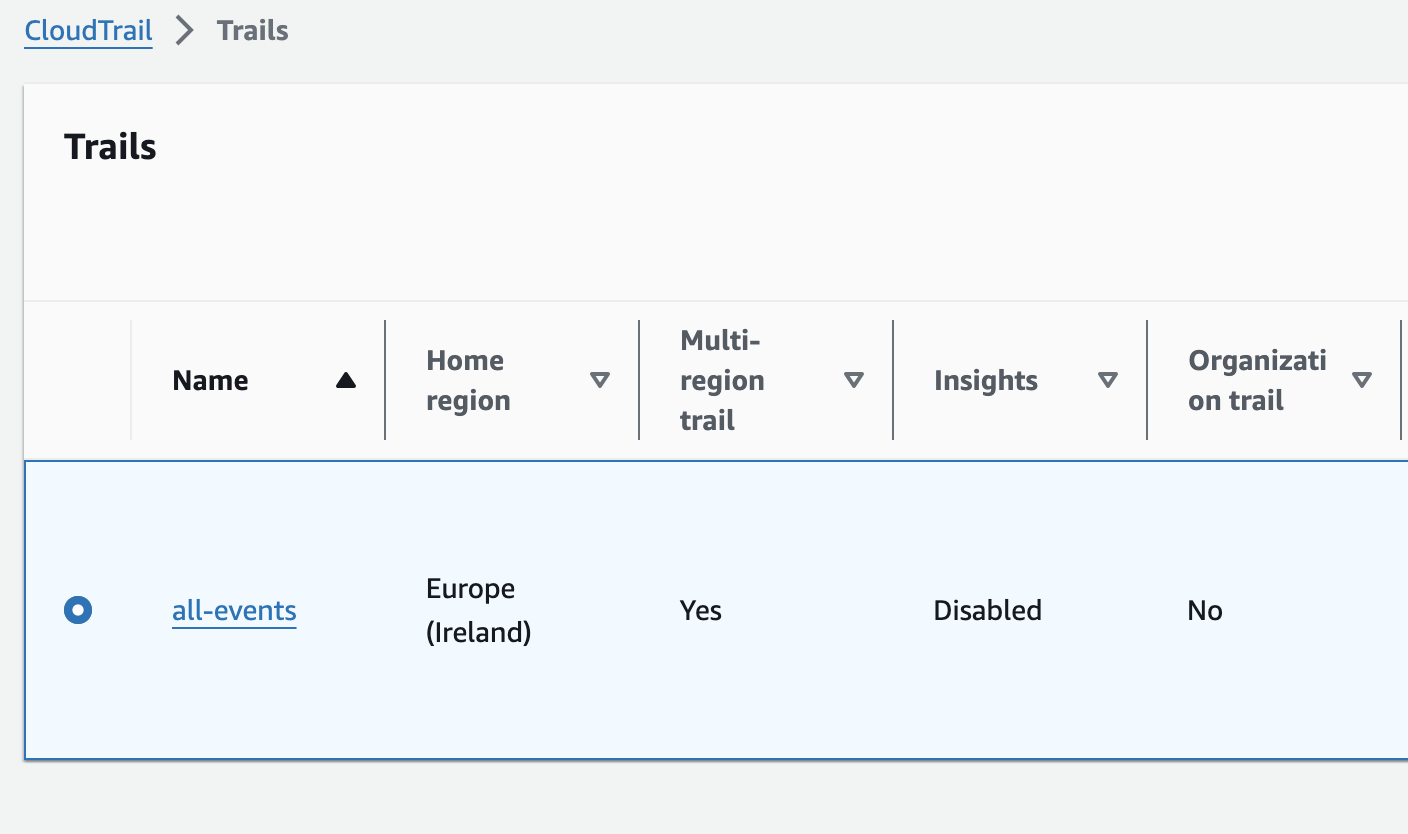
- Trails, that capture events and deliver them to Amazon S3 buckets. Additionally, you can enable event delivery to Amazon CloudWatch or Amazon EventBridge.
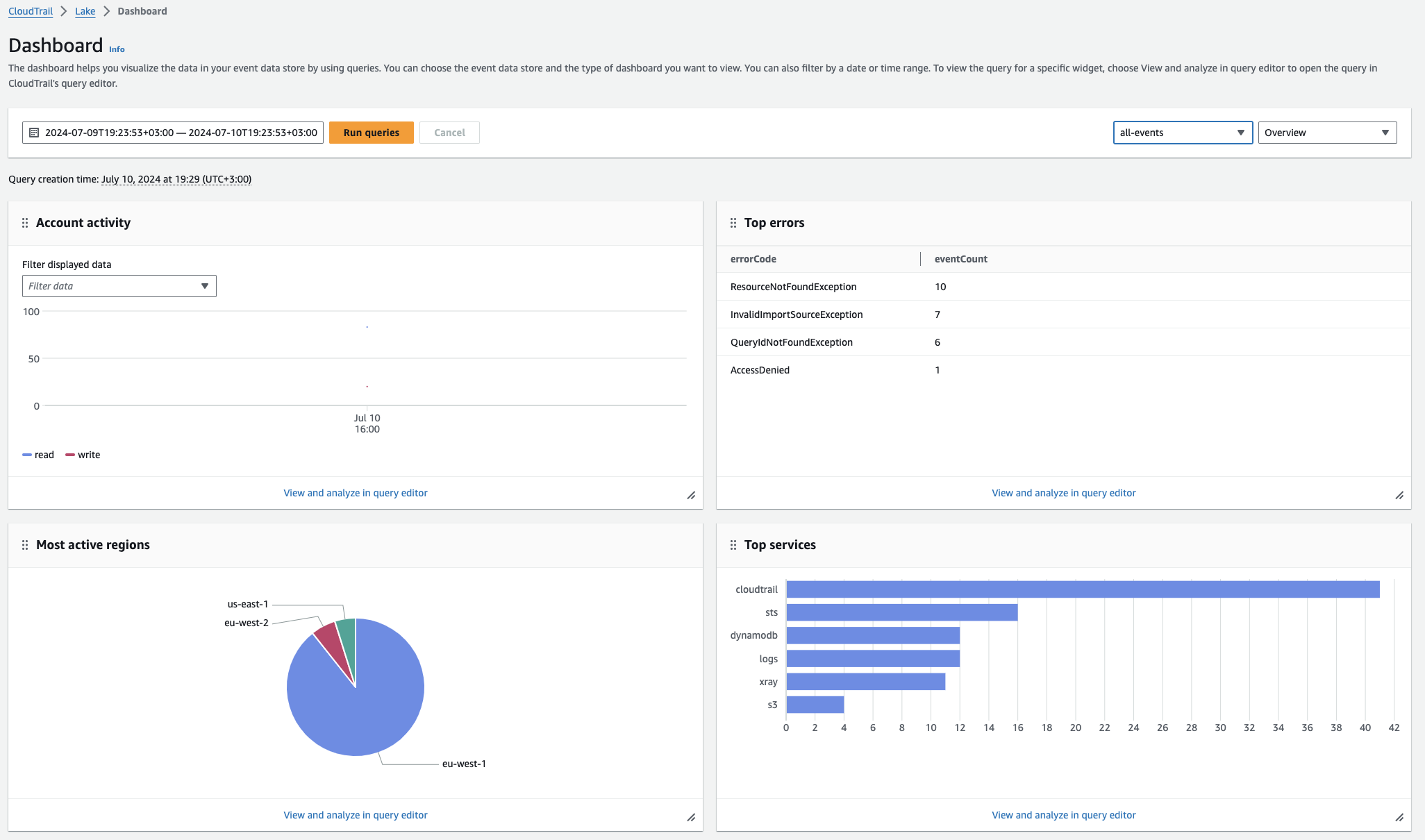
- CloudTrail Lake, a managed data lake for capturing, storing, accessing, and analyzing events.
There are three types of events:
- Management events provide an overview of different operations performed on AWS resources in your AWS account. For example, listing S3 buckets (
ListBuckets) , describing subnets (DescribeSubnets), creating new EC2 instance (RunInstances) etc. - Data events provide details about the operations performed on specific resources (also known as data plane operations). For example, get object from S3 bucket (
GetObject), invoke lambda function (Invoke) , send message to SNS topic (Publish) - Insights events are logged only when CloudTrail notices changes in your account's API usage that differ from usual patterns.
12 AWS CloudTrail Best Practices
To optimize the benefits of CloudTrail and improve security, it's important to follow some best practices tips, which we will now describe.
Create a Trail in All AWS Accounts and Regions
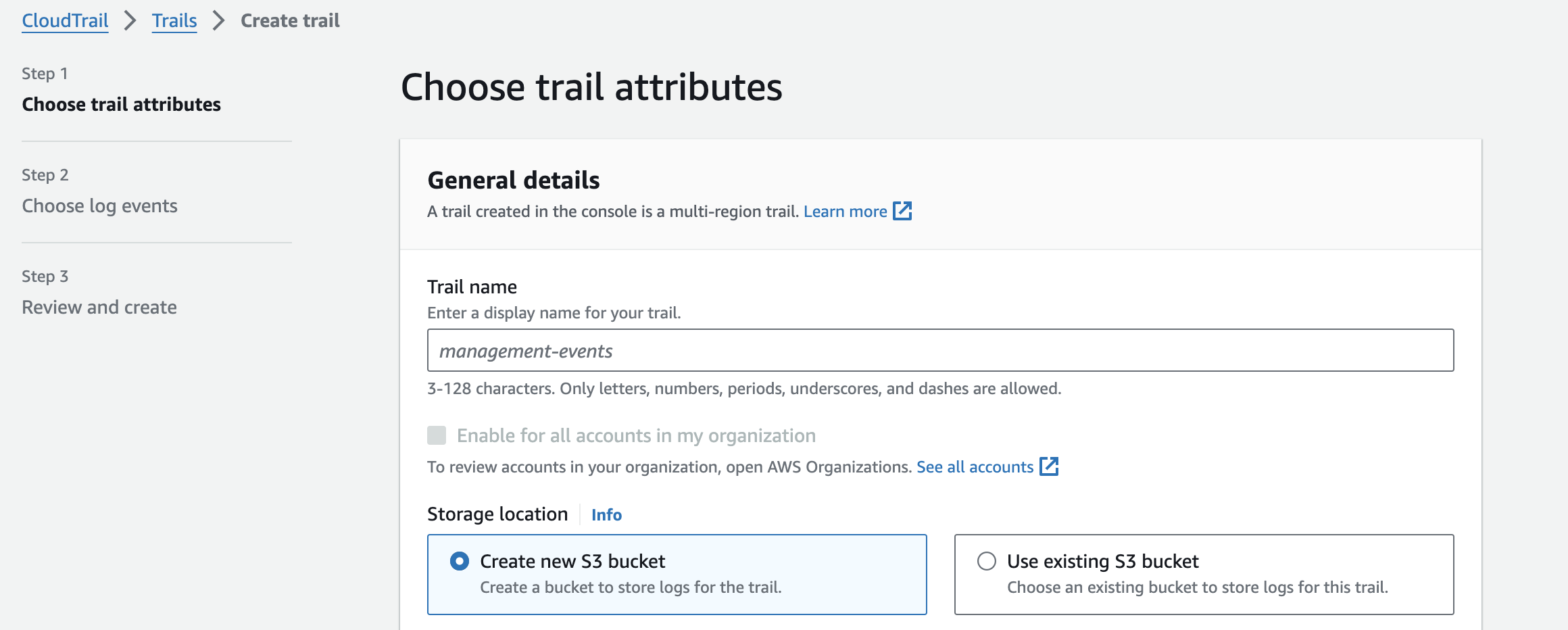
While AWS CloudTrail automatically provides every AWS account with management event history for the last 90 days, it is recommended to create a trail to record all events initiated by a user, role, or service in your AWS account. By creating a trail, you can specify an Amazon S3 bucket where the events will be stored. Optionally, you can choose CloudWatch Logs or Amazon EventBridge for event delivery. Events are stored as JSON objects. Here is an example of a "list S3 buckets" event:
{
"eventVersion": "1.08",
"userIdentity": {
"type": "AssumedRole",
"principalId": "XXXXXXXXXXXXXXX:username",
"arn": "arn:aws:sts::123456789012:assumed-role/RoleName/username",
"accountId": "123456789012",
"accessKeyId": "XXXXXXXXXXXXXXXX",
"sessionContext": {
"sessionIssuer": {
"type": "Role",
"principalId": "XXXXXXXXXXXXXXX",
"arn": "arn:aws:iam::123456789012:role/RoleName",
"accountId": "123456789012",
"userName": "RoleName"
},
"webIdFederationData": {},
"attributes": {
"creationDate": "2024-07-11T00:00:00Z",
"mfaAuthenticated": "false"
}
}
},
"eventTime": "2024-07-11T00:00:00Z",
"eventSource": "s3.amazonaws.com",
"eventName": "ListBuckets",
"awsRegion": "us-west-2",
"sourceIPAddress": "192.0.2.0",
"userAgent": "aws-cli/2.0.0 Python/3.7.3 Windows/10 botocore/2.0.0",
"requestParameters": null,
"responseElements": null,
"requestID": "EXAMPLE123456789",
"eventID": "event-id-2-3-4-5",
"eventType": "AwsApiCall",
"recipientAccountId": "123456789012",
"eventCategory": "Management"
}When you create a trail in the AWS console, it is automatically created as a multi-region trail. This means that CloudTrail will record all events in all AWS regions and deliver them to a specified S3 bucket.
We should create a trail for all AWS accounts and regions to gain complete visibility of what is happening inside your AWS environments. If you use AWS Organizations to manage AWS accounts, it is possible to create one trail that logs all events for all AWS accounts in that organization.
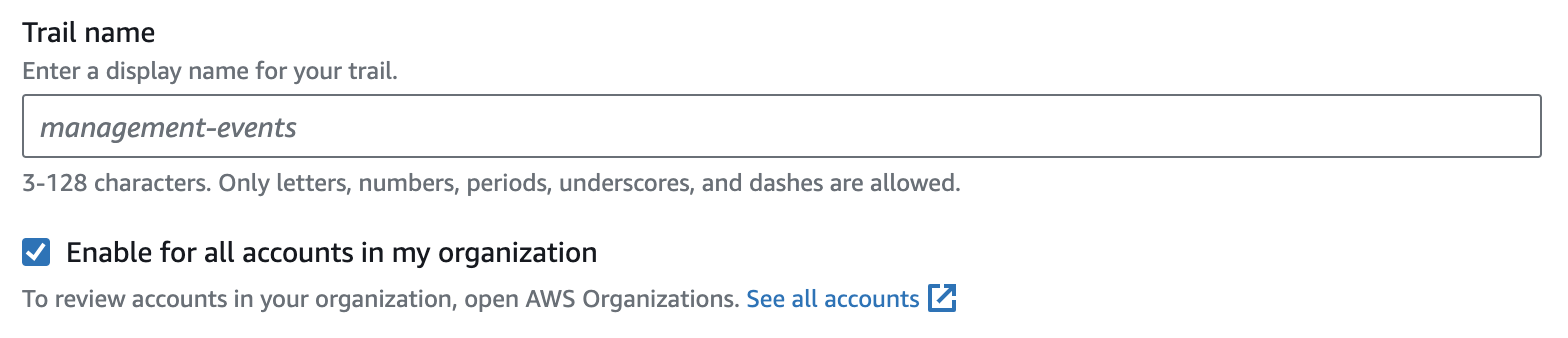
Of course, always consider CloudTrail pricing and the costs for using additional AWS services like S3, CloudWatch, SNS, EventBridge, etc.
Set up Separate Trails for Different Use Cases
Organizations use CloudTrail for multiple use cases such as security monitoring, operational troubleshooting, and auditing. If these use cases are managed by different teams, it is recommended to create multiple trails with varied configurations (such as retention policy, access rights, and additional logging like sending logs to CloudWatch and enabling S3 bucket access logging) and to deliver events to different S3 buckets.
For instance, a security team responsible for overall security monitoring can create a trail that records events across all AWS accounts and regions. Meanwhile, a specific product team responsible for developing one of the organization's products can create a trail for a specific AWS account and region related to their product.
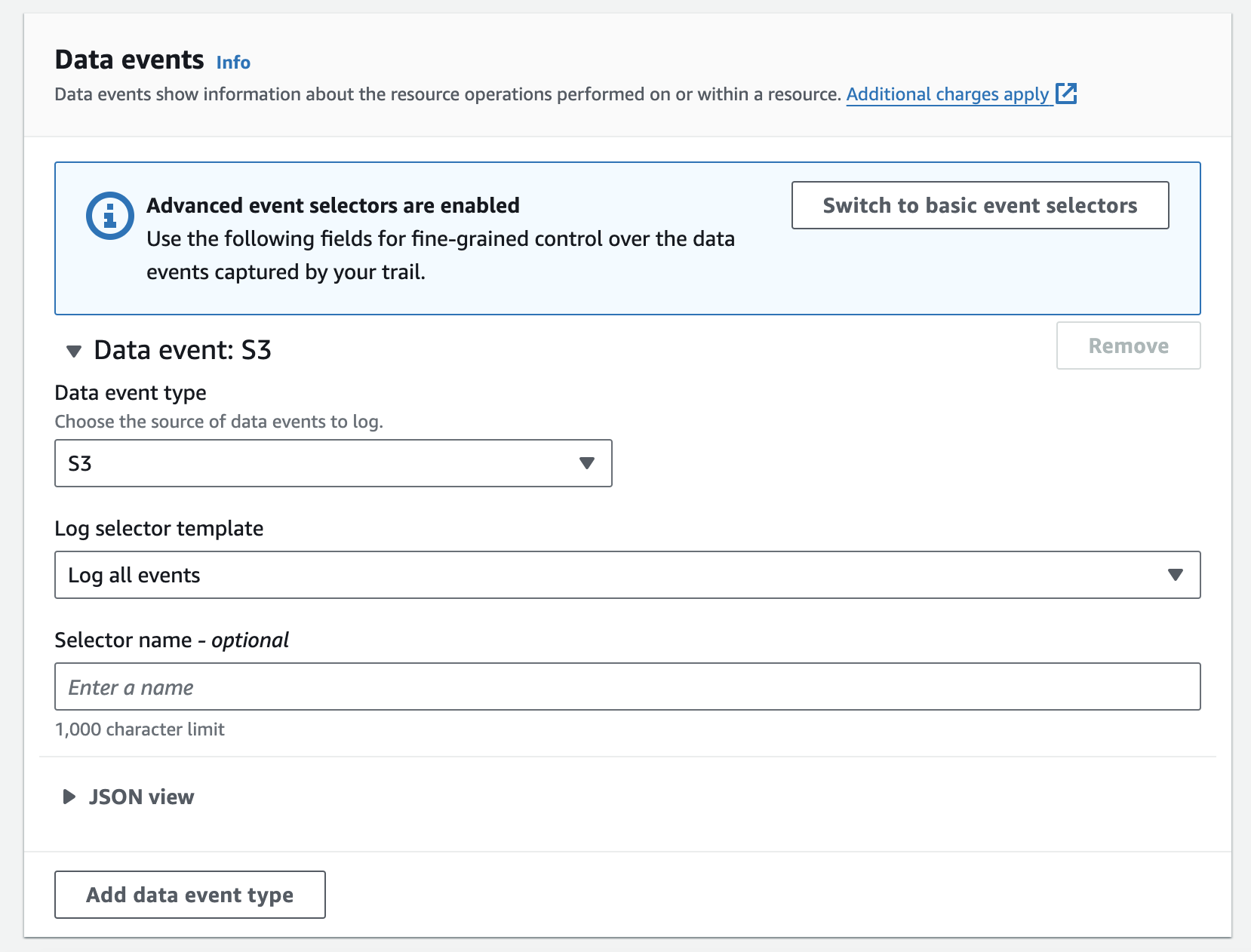
Turn on Data Events for Trails
As mentioned previously, data events provide details about operations performed on specific resources, such as retrieving an S3 object, invoking a Lambda function, or sending a message to an SNS topic. While this may not be necessary for all trails and use cases, there is a solid chance that your application handles sensitive data. You may want to log who accessed that data and when, to limit the possibility of unexpected access.
To avoid recording all data events (which are often high-volume), it is best practice to use advanced event selectors to specify exactly which events you want to log.
Store CloudTrail Events in a Dedicated and Centralized S3 Bucket
CloudTrail trail events should be stored in a dedicated S3 bucket. It is important to enforce strict access controls on who can access this S3 bucket. When you have multiple AWS accounts, a best practice is to use a dedicated centralized logging account. This account would contain not only CloudTrail event history but also VPC flow logs, AWS Config logs, CloudWatch logs, and more.
Use CloudTrail Log File Integrity Validation
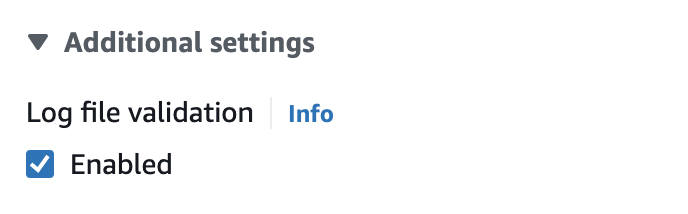 We should enable log file validation when creating a CloudTrail trail. This will help determine whether a log file (events file) was modified, deleted, or left unchanged after it was delivered to the S3 bucket.
We should enable log file validation when creating a CloudTrail trail. This will help determine whether a log file (events file) was modified, deleted, or left unchanged after it was delivered to the S3 bucket.
Send CloudTrail Events to CloudWatch Logs
 In order to make CloudTrail logs actionable, we should send events to CloudWatch Logs. This allows us to analyze and create alerts for specific events in near real time. For example, we can create a metric for security group changes using event names like
In order to make CloudTrail logs actionable, we should send events to CloudWatch Logs. This allows us to analyze and create alerts for specific events in near real time. For example, we can create a metric for security group changes using event names like AuthorizeSecurityGroupIngress, DeleteSecurityGroup, and CreateSecurityGroup. Based on this metric, we can create an alert to notify the security team whenever this metric changes.
Configure Least Privilege Access to the CloudTrail Logs S3 Bucket
As we discussed in a previous article on how to improve the security of your AWS account, IAM identities (with IAM policies) often have more access rights than needed to fulfill a specific use case or task. The same principle applies to setting least privilege access to the CloudTrail logs S3 bucket. Access to CloudTrail logs should only be granted to a limited number of users, teams, or services who have a valid reason for viewing the logs.
Enable MFA delete on the CloudTrail Logs S3 Bucket
Multi-factor authentication has been around for a while and should be enabled for any application that processes private data. Just as you would use MFA during the initial user authentication process, you should configure MFA for the CloudTrail logs S3 bucket when users try to delete or change the version of an object. This helps prevent unauthorized operations on our log files, even if a user's password is compromised.
Define a Retention Policy for Logs Stored in S3
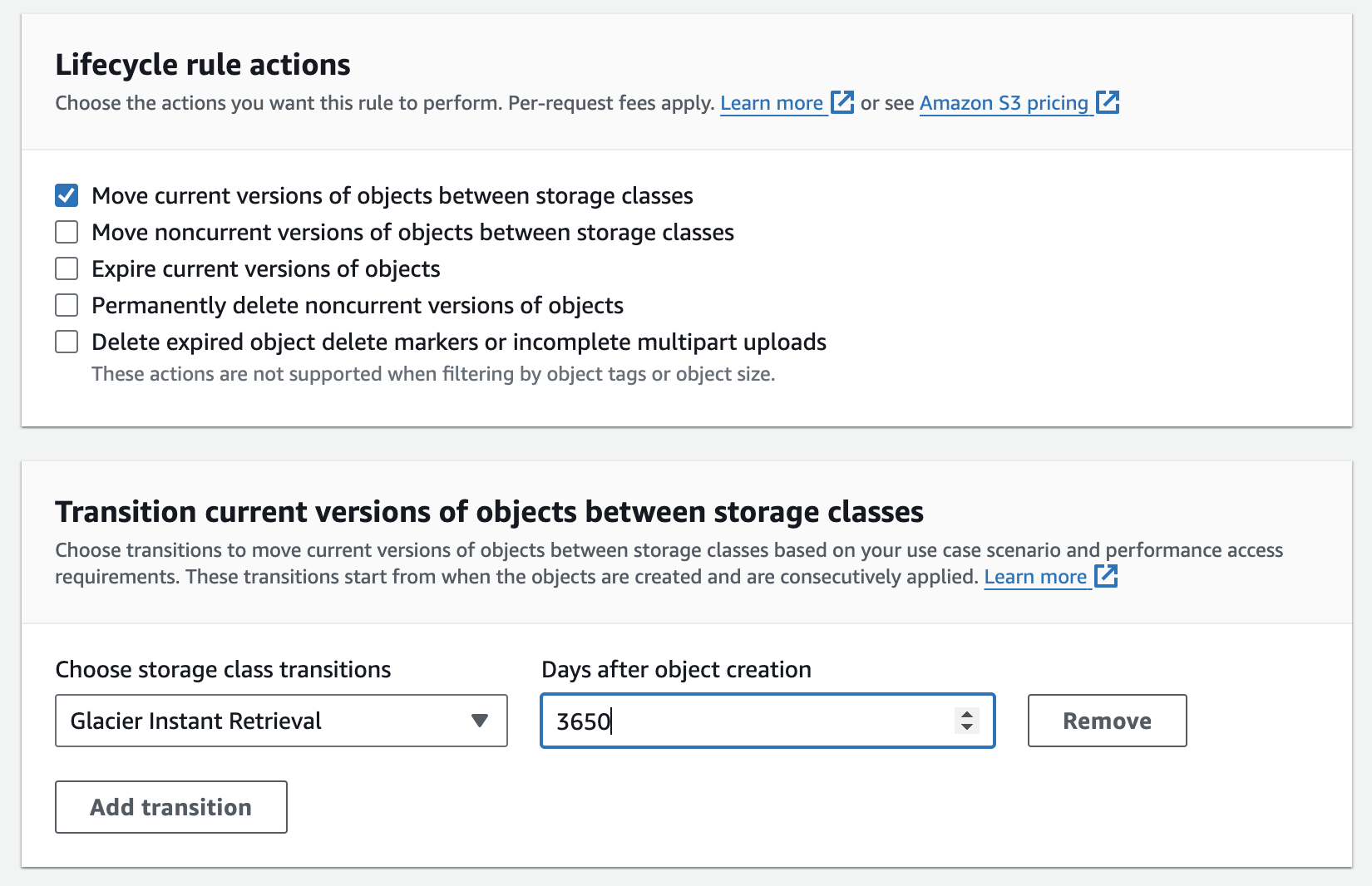
CloudTrail trail logs are stored indefinitely in the dedicated S3 bucket. While this can be a good approach for many organizations, different compliance requirements may require setting a specific retention policy. You can easily achieve this by using S3 object lifecycle rules. For example, you may need to keep log files for 10 years and then move them to an archive using Amazon Glacier, or you may need to keep log files for only 3 years before it becomes mandatory to delete them.
Encrypt CloudTrail Log Files at Rest
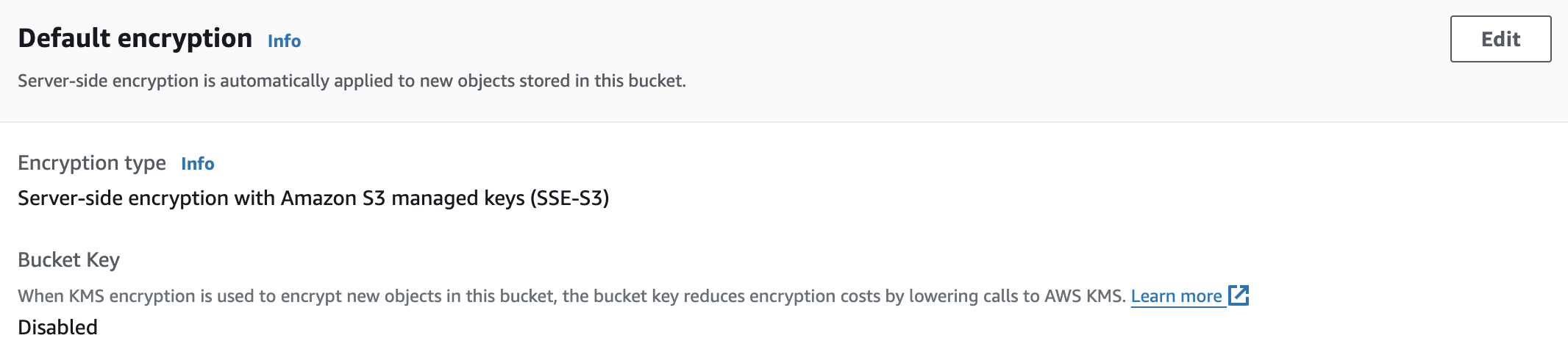
Starting on January 5, 2023, all new S3 object uploads (in our case, CloudTrail log files) are encrypted using Amazon S3 managed encryption keys (SSE-S3) at no additional cost of configuration. If there is a requirement for more control over log file security, it’s possible to use KMS keys stored in AWS KMS (SSE-KMS).
Enable Logging on the CloudTrail S3 Bucket
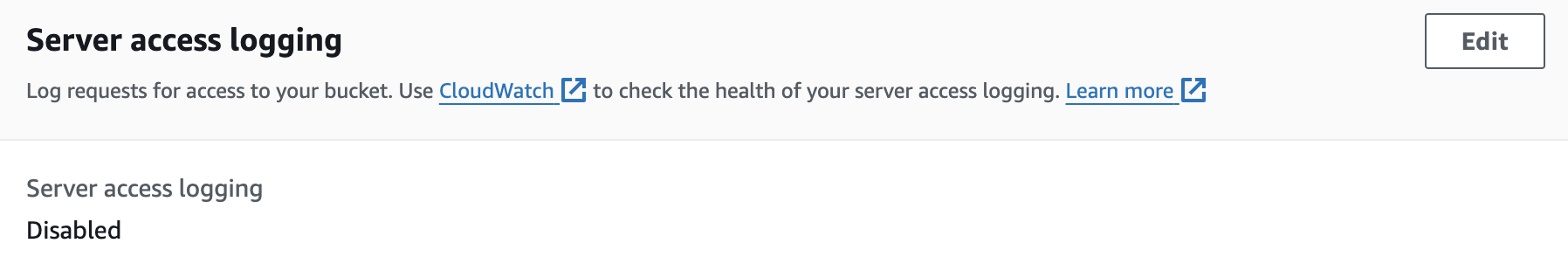
By enabling server access logging for the CloudTrail logs S3 bucket, we can understand who accessed our CloudTrail logs and when. These logs are stored in a different bucket with specific access controls for a limited number of users. Server access log information can be useful for security and access audits.
Limit Usage of the AWSCloudTrail_FullAccess policy
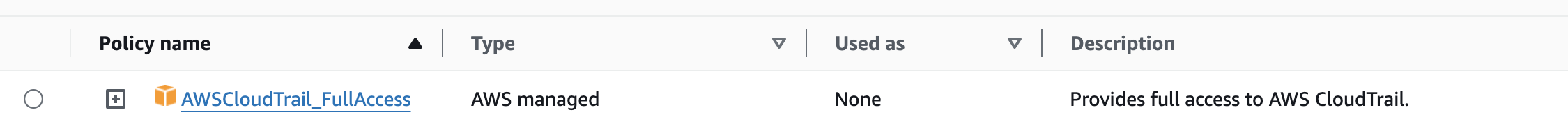
Limit the usage of the IAM policy AWSCloudTrail_FullAccess to as few users as possible. This policy grants administrator access to the CloudTrail service, allowing users to disable and reconfigure logging settings for your AWS account.
AWS CloudTrail Costs
As I mentioned previously, CloudTrail provides 90 days of management event history by default for every AWS account and region for free. While this is a good start, most organizations will need to create a trail or start a CloudTrail Lake to comply with all the necessary audit, security, retention, and compliance requirements. This is where CloudTrail costs start to come into play.
The main CloudTrail costs are calculated based on:
- For Trails: The number of management or data events delivered to Amazon S3
- For CloudTrail Lake: GBs of data ingestion, retention, and data queries
There is one free trail available that can record management events for free (excluding all Amazon S3 related costs). However, in many use cases, you will have multiple trails and data events enabled, which can become expensive.
I recommend always monitoring your AWS costs to minimize the risk of an unpleasant surprise when you receive your next AWS invoice.
Summary
While AWS CloudTrail is enabled by default for all AWS accounts and provides 90 days of management event history, this is not sufficient for organizations that use CloudTrail for audit, compliance, and security purposes. In this article, we described 12 AWS CloudTrail best practices that can be easily implemented to maximize the benefits CloudTrail can provide to organizations. I would like to especially highlight two points that every organization should pay extra attention to: always limit and secure access to CloudTrail logs history, and always monitor CloudTrail costs.
Tired of browsing through the AWS console?
Try out Cloudviz.io and visualize your AWS cloud environment in seconds

As experienced AWS architects and developers, our mission is to provide users an easy way to generate stunning AWS architecture diagrams and detailed technical documentation. Join us to simplify your diagramming process and unleash the beauty of your cloud infrastructure
Support
Contact
Copyright © 2019 - 2025 Cloudviz Solutions SIA