15 AWS Config Rules Every AWS Account Should Have

by Valts Ausmanis · July 5, 2024
Every application that we deploy to AWS is built using multiple AWS services like API Gateway, Lambda, S3, EC2, EKS, VPC, etc. All of these deployed services consist of multiple AWS resources. To ensure that your AWS account is secure and follows to certain security checks, it’s important to track changes of these resources and continuously assess if the resource configuration complies with your ideal security rules. Luckily, we have AWS Config to record changes and assess your AWS resource configurations. In this article, we will look at how to start using AWS Config and set up 15 AWS Config rules that should be considered for any AWS account.
In This Article
- What is AWS Config?
- How to Enable AWS Config?
- 15 AWS Config Rules Every AWS Account Should Have
- s3-bucket-public-read-prohibited
- access-keys-rotated
- iam-user-unused-credentials-check
- root-account-mfa-enabled
- ec2-instance-no-public-ip
- rds-instance-public-access-check
- vpc-default-security-group-closed
- iam-password-policy
- ec2-ebs-encryption-by-default
- s3-bucket-server-side-encryption-enabled
- dynamodb-table-encryption-enabled
- rds-storage-encrypted
- lambda-function-public-access-prohibited
- acm-certificate-expiration-check
- vpc-flow-logs-enabled
- cloudtrail-enabled
- Consider AWS Config Costs
- Summary
What is AWS Config?
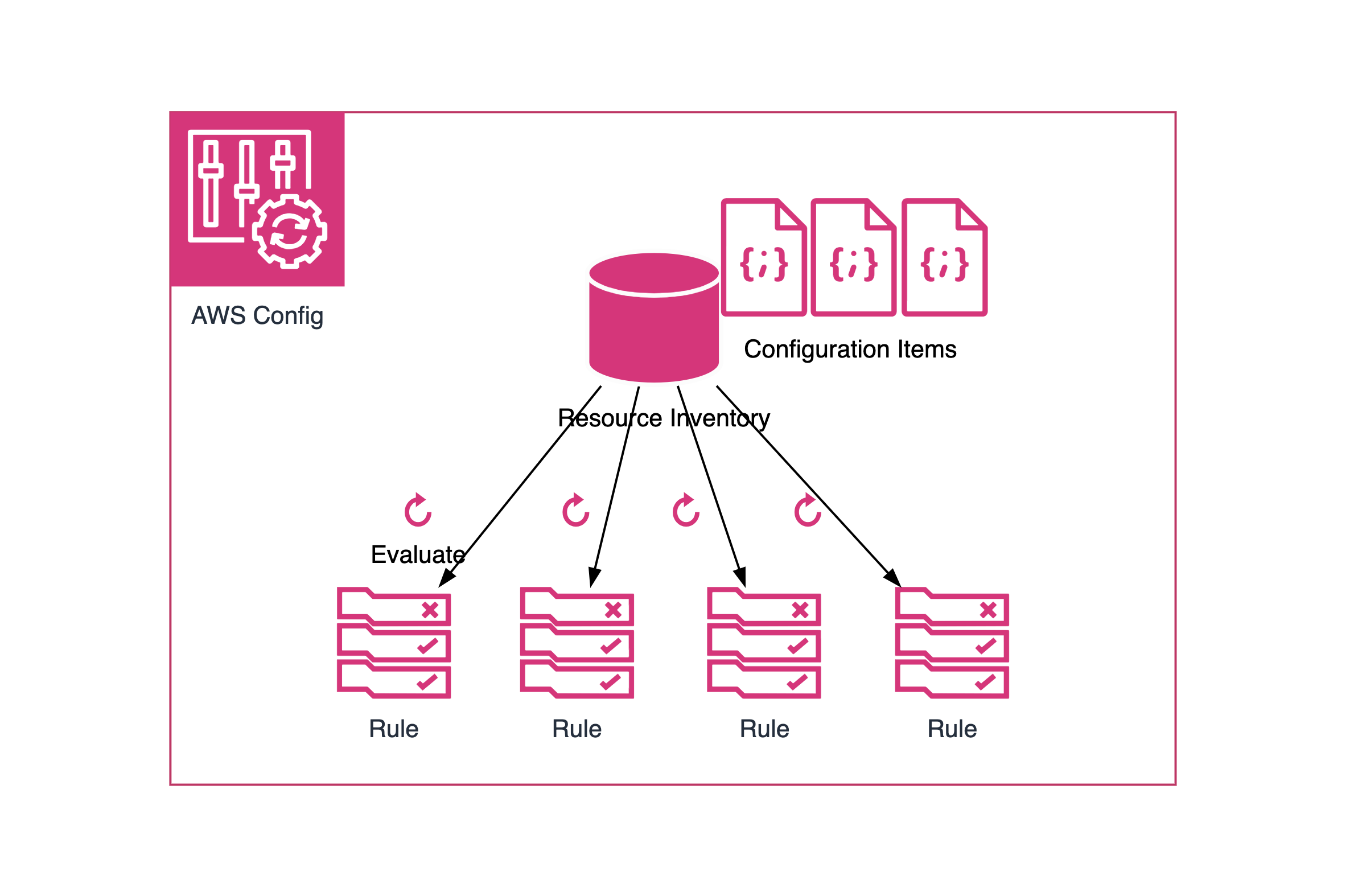
AWS Config ensures that we have an always up-to-date AWS resource inventory that is constantly evaluated against your ideal security rules, which is a must-have for every organization, regardless of its size. Its two main tasks are:
- Record AWS resource changes, called configuration items, whenever there is a configuration or relationship change.
- Evaluate if the resource configuration item complies with your enabled AWS Config rules. You can choose from AWS managed rules or write your own rules using custom policies or custom lambda functions.
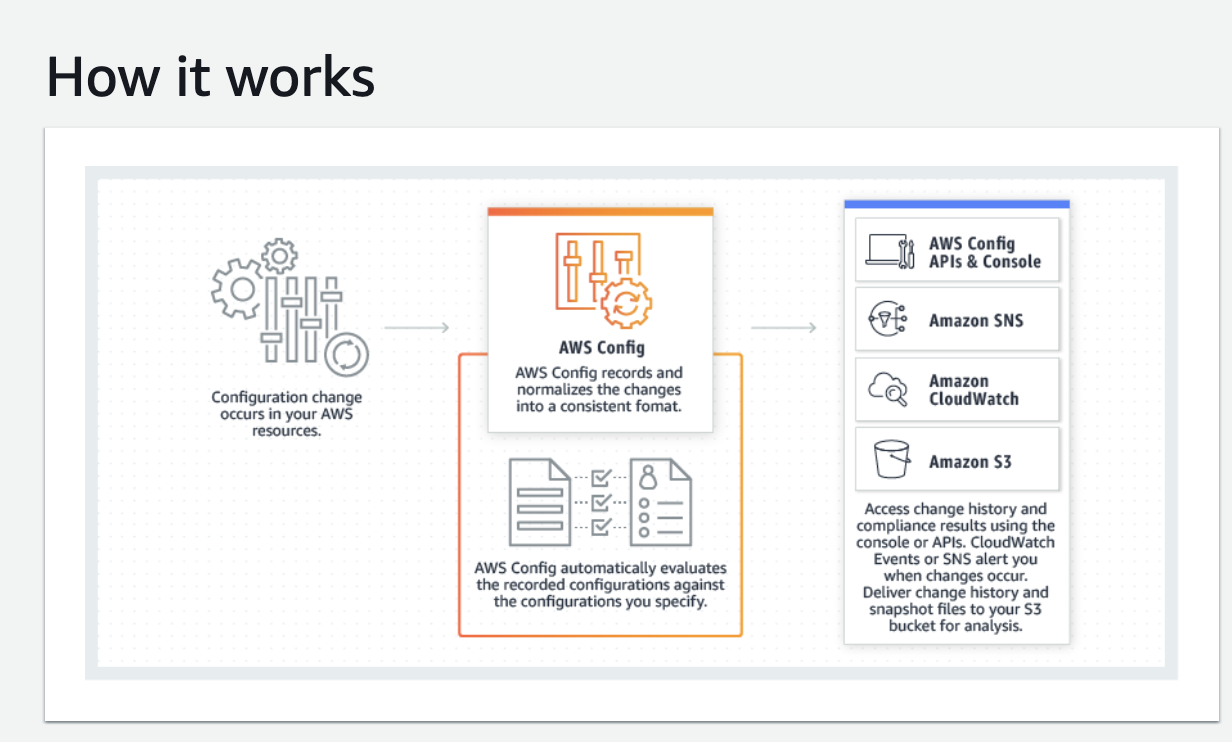
How to Enable AWS Config?
To enable AWS Config to start recording AWS resource configuration changes, navigate to AWS Config settings and:
- Enable recording.
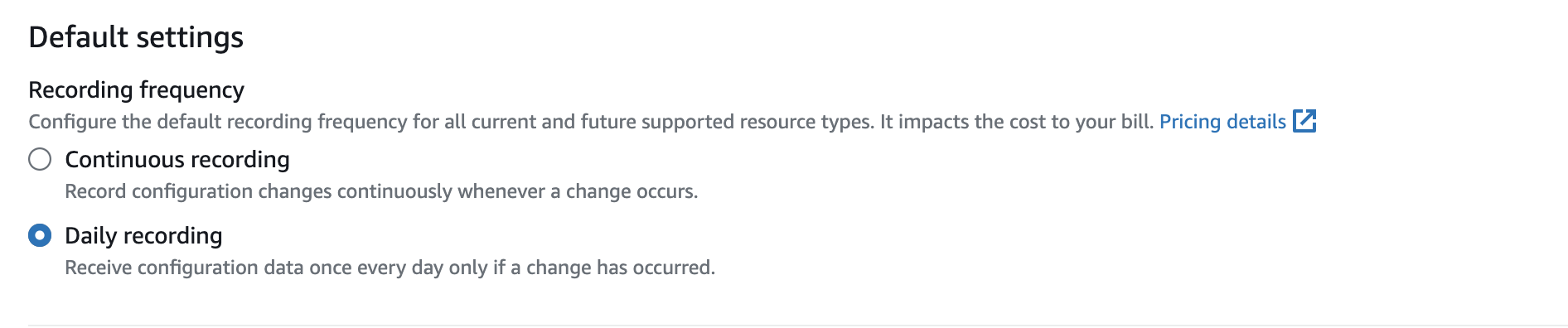
- Based on your preference you have to set your recording strategy:
- Periodic recording: Records configuration data every 24 hours if there's a change, useful for planning or audits.
- Continuous recording: Records configuration changes as they happen.
 You can also choose to record or exclude specific resource types, such as S3 buckets, VPCs, subnets, etc. This can be useful if your application uses temporary AWS resources that are deployed and then deleted from your account (e.g., Spot Instances, AWS Auto Scaling resources).
You can also choose to record or exclude specific resource types, such as S3 buckets, VPCs, subnets, etc. This can be useful if your application uses temporary AWS resources that are deployed and then deleted from your account (e.g., Spot Instances, AWS Auto Scaling resources). - Choose the delivery method for configuration changes. The mandatory default is an S3 bucket, and optionally, you can stream configuration changes to an SNS topic or create Amazon EventBridge rules
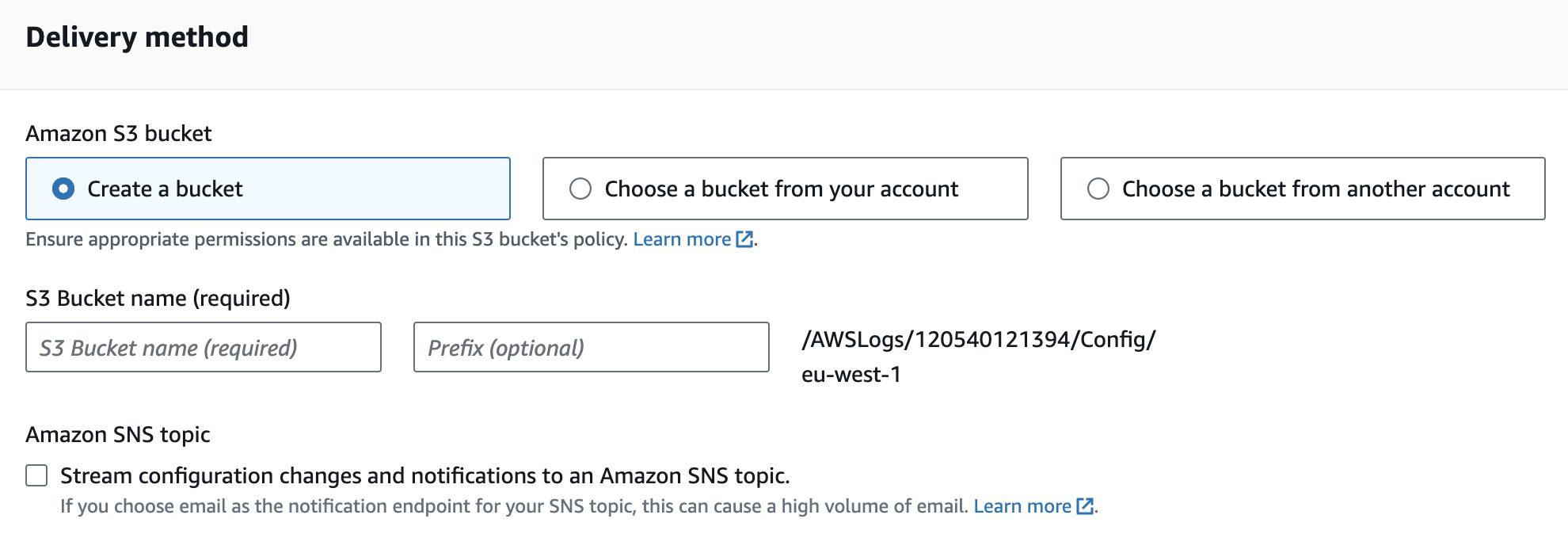
15 AWS Config Rules Every AWS Account Should Have
Once the AWS Config resource recorder is enabled, the next step is to add AWS Config rules. This ensures that our AWS resources comply with our ideal configuration settings.
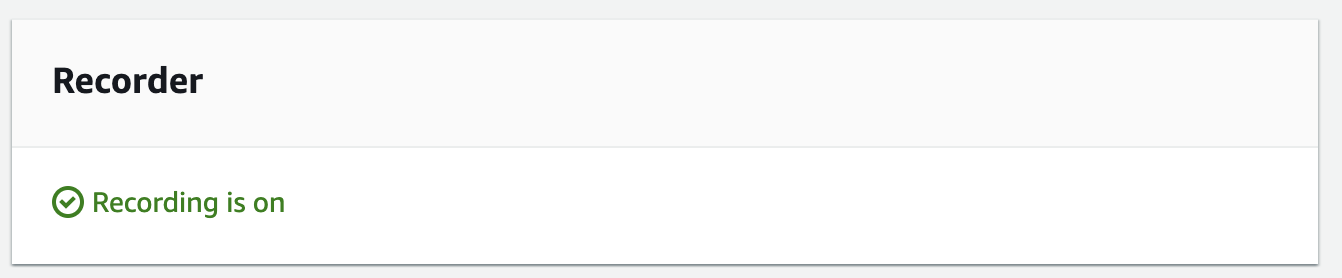
There are around 390 AWS Config managed rules that you can add. While it might be tempting to add as many rules as possible, I suggest starting with the minimum set of rules that should be enabled for any AWS account. Once the base rules are in place, evaluate your application's security requirements and add additional AWS Config rules as needed. This is a continuous process, and you should regularly evaluate the rules, especially when making significant changes to your application.
Now, let’s take a look at 15 AWS Config rules that every AWS account should have.
s3-bucket-public-read-prohibited
 This rule checks that your S3 buckets do not allow public read access. While today, when you create a new S3 bucket, by default, all new buckets are private — I still would enable this rule and double-check it.
This rule checks that your S3 buckets do not allow public read access. While today, when you create a new S3 bucket, by default, all new buckets are private — I still would enable this rule and double-check it.
access-keys-rotated
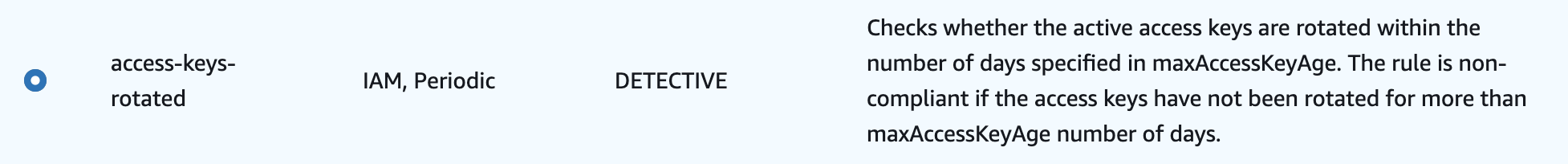 Ensures IAM user access keys are rotated. While we shouldn’t use persistent credentials at all and should use temporary ones instead, if there is still a need to use them, ensure that you rotate them frequently.
Ensures IAM user access keys are rotated. While we shouldn’t use persistent credentials at all and should use temporary ones instead, if there is still a need to use them, ensure that you rotate them frequently.
iam-user-unused-credentials-check
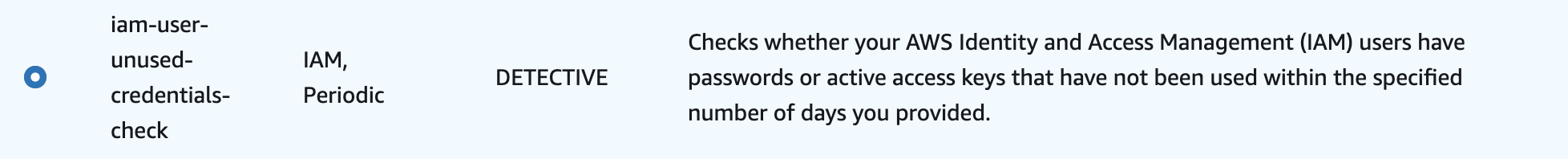 This rule checks if your IAM users' passwords or access keys haven’t been used for a while. Again, I wouldn’t create IAM users or access keys at all and use AWS IAM Identity Center to manage access to my AWS accounts, but if you use these at least ensure that this rule is added.
This rule checks if your IAM users' passwords or access keys haven’t been used for a while. Again, I wouldn’t create IAM users or access keys at all and use AWS IAM Identity Center to manage access to my AWS accounts, but if you use these at least ensure that this rule is added.

root-account-mfa-enabled
 Checks that multi-factor authentication (MFA) is enabled for the root account. Due to the over-permissive privileges, we shouldn’t use root user at all except for a few specific use cases.
Checks that multi-factor authentication (MFA) is enabled for the root account. Due to the over-permissive privileges, we shouldn’t use root user at all except for a few specific use cases.
ec2-instance-no-public-ip
 Checks that EC2 instances do not have a public IP address. Security best practices suggests that you should avoid using EC2 instances with unnecessary public IP addresses in order to reduce the attack surface.
Checks that EC2 instances do not have a public IP address. Security best practices suggests that you should avoid using EC2 instances with unnecessary public IP addresses in order to reduce the attack surface.
rds-instance-public-access-check
 Ensures RDS instances are not publicly accessible . EC2 instances, Lambda functions, ECS tasks, etc. should access our RDS databases via a private network (VPC), ensuring that DB connections and data transfer do not go over the public internet.
Ensures RDS instances are not publicly accessible . EC2 instances, Lambda functions, ECS tasks, etc. should access our RDS databases via a private network (VPC), ensuring that DB connections and data transfer do not go over the public internet.
vpc-default-security-group-closed
 Checks that the default security group of every VPC does not allow inbound or outbound traffic.
Checks that the default security group of every VPC does not allow inbound or outbound traffic.
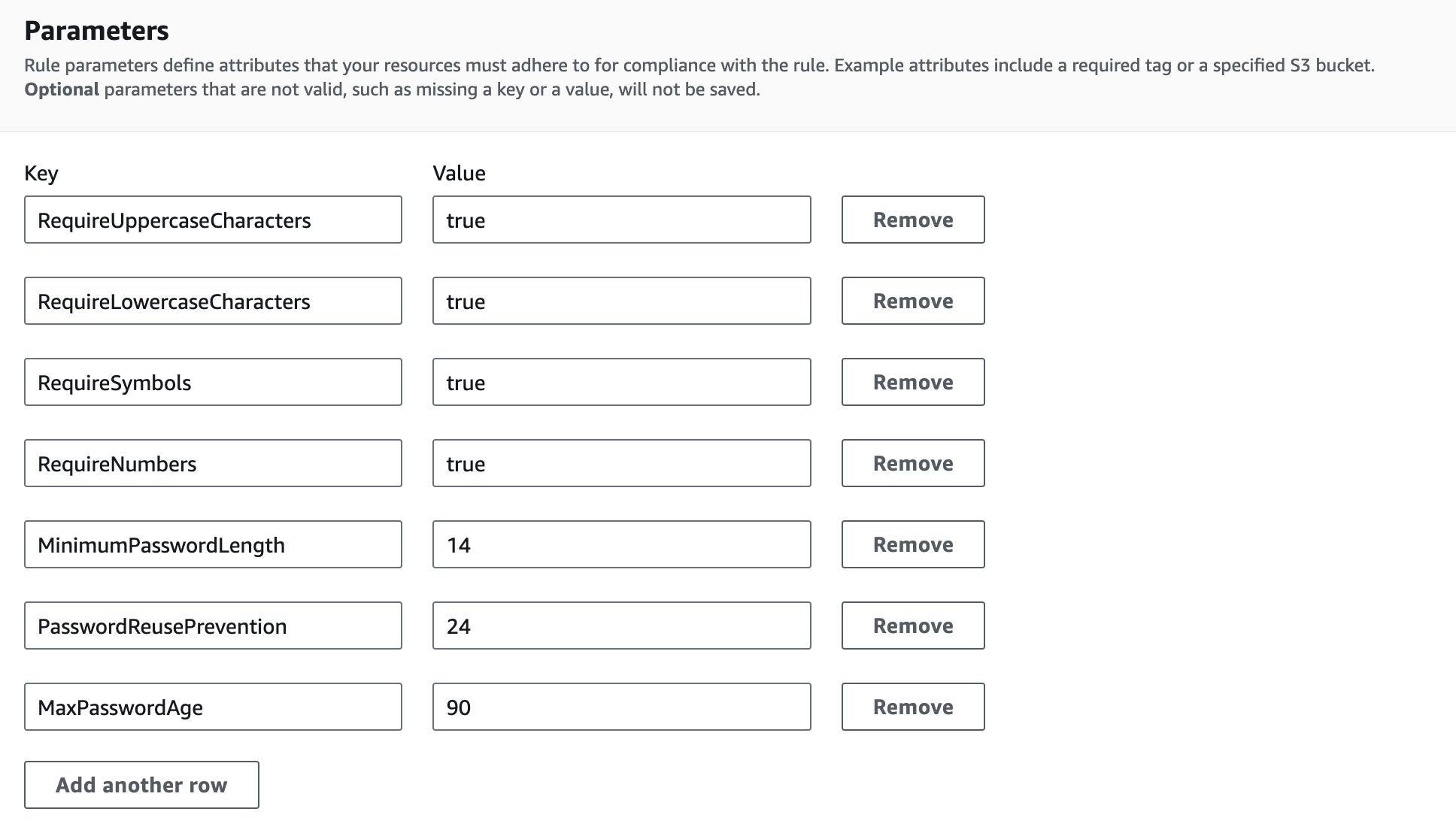
iam-password-policy
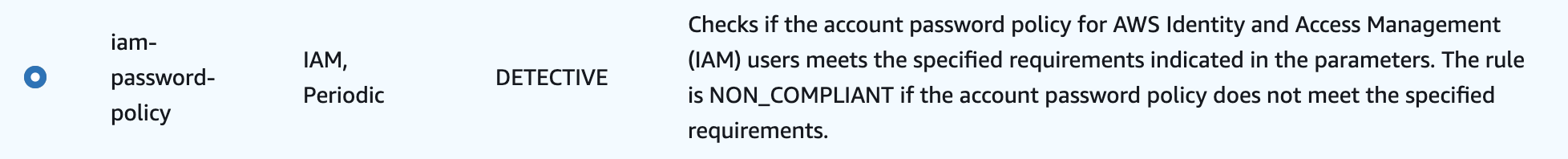 This rule ensures that your IAM password policy requires a minimum password length and includes specific character types. The fact that our AWS accounts should have a configured IAM password policy is not in question. By enabling this rule, we ensure additionally that there is a policy that meets certain requirements.
This rule ensures that your IAM password policy requires a minimum password length and includes specific character types. The fact that our AWS accounts should have a configured IAM password policy is not in question. By enabling this rule, we ensure additionally that there is a policy that meets certain requirements.
ec2-ebs-encryption-by-default
 Checks that EBS encryption is enabled by default. This setting ensures that whenever you create new EBS volume – encryption will be enabled by default.
Checks that EBS encryption is enabled by default. This setting ensures that whenever you create new EBS volume – encryption will be enabled by default.
s3-bucket-server-side-encryption-enabled
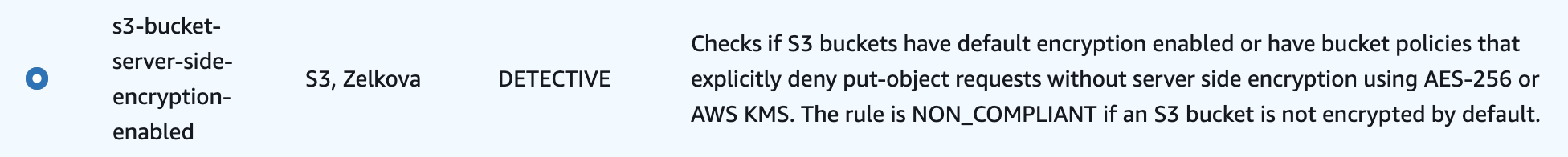 This rule ensures that S3 should be encrypted by default.
This rule ensures that S3 should be encrypted by default.
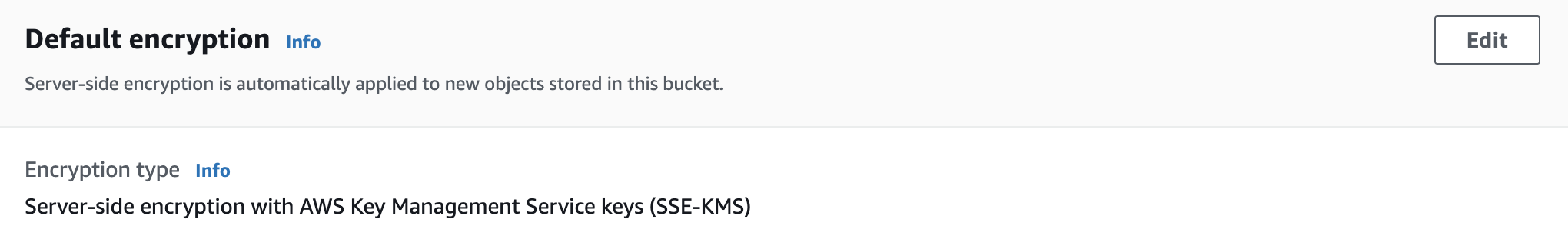
dynamodb-table-encryption-enabled
 Ensures that DynamoDB tables are encrypted at rest.
Ensures that DynamoDB tables are encrypted at rest.
rds-storage-encrypted
 Checks that RDS storage is encrypted. While most AWS services have encryption at rest enabled by default, it is still recommended to include storage encryption checks as part of best practices.
Checks that RDS storage is encrypted. While most AWS services have encryption at rest enabled by default, it is still recommended to include storage encryption checks as part of best practices.
lambda-function-public-access-prohibited
 Ensures Lambda functions are not publicly accessible. If you grant access to your Lambda functions to other AWS accounts, it is suggested that you have this rule in place to ensure that the access policy doesn’t contain a wildcard. For example, the principal element should not be
Ensures Lambda functions are not publicly accessible. If you grant access to your Lambda functions to other AWS accounts, it is suggested that you have this rule in place to ensure that the access policy doesn’t contain a wildcard. For example, the principal element should not be "" or { "AWS": ""}.
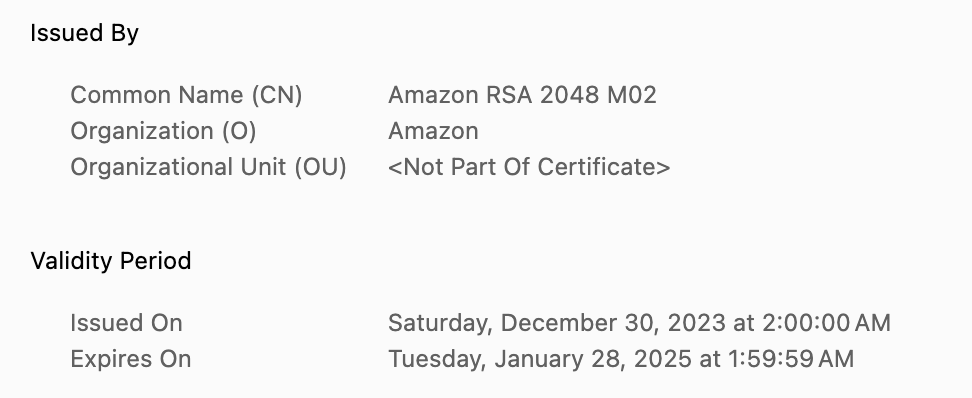
acm-certificate-expiration-check
 Checks whether ACM certificates in your account are marked for expiration within a specific number of days. This rule is especially important for manually imported certificates that ACM does not renew automatically.
Checks whether ACM certificates in your account are marked for expiration within a specific number of days. This rule is especially important for manually imported certificates that ACM does not renew automatically.
vpc-flow-logs-enabled
 Checks that VPC flow logs are enabled. Whenever you use Amazon VPC for your back-end services, you should consider enabling flow logs. This will help with your audit process and, of course, troubleshooting when something goes wrong.
Checks that VPC flow logs are enabled. Whenever you use Amazon VPC for your back-end services, you should consider enabling flow logs. This will help with your audit process and, of course, troubleshooting when something goes wrong.
cloudtrail-enabled
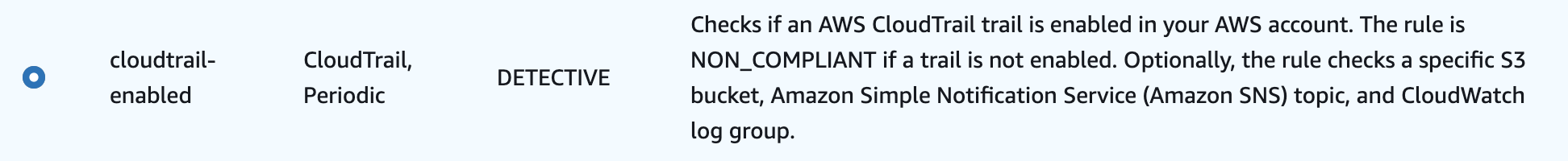 Ensures AWS CloudTrail is enabled. CloudTrail logs contain details about all the API calls made within your AWS account (including usage in the AWS console). These logs can then be used to track changes, troubleshoot security incidents, and ensure compliance with your internal policies.
Ensures AWS CloudTrail is enabled. CloudTrail logs contain details about all the API calls made within your AWS account (including usage in the AWS console). These logs can then be used to track changes, troubleshoot security incidents, and ensure compliance with your internal policies.
Consider AWS Config Costs
While AWS Config does a great job recording and assessing resource configuration changes, it can get expensive if you have many resources that change frequently. Your AWS Config costs are based on two main usage types:
- Cost per recorded configuration item
- Cost per rule evaluation
I suggest to closely monitor usage costs for AWS config and then optimize your settings, for example, disable or update some “expensive” rules, exclude unnecessary resources, change configuration item recording schedule to Periodic etc.
Summary
With AWS Config you can start to record changes of your AWS resources with few simple clicks and have a nice AWS resource inventory up and running in no time. The more challenging part is to enable right AWS config rules. There are around 390 AWS Config managed rules to choose from, and it can be easy to get confused when you start adding AWS Config rules. That’s why I created and described in detail a list of 15 AWS Config rules that you should add to any AWS account. This will provide a good foundation to start improving your security posture. By using AWS Config, we are taking another step in the continuous journey of improving the security of our AWS accounts.
Looking for tool to automatically track your cloud infrastructure changes?
Try out Cloudviz.io and have your infrastructure change history whenever you need it

As experienced AWS architects and developers, our mission is to provide users an easy way to generate stunning AWS architecture diagrams and detailed technical documentation. Join us to simplify your diagramming process and unleash the beauty of your cloud infrastructure
Support
Contact
Copyright © 2019 - 2025 Cloudviz Solutions SIA